Network management software
Rene Millman delves into the world of network management software and discovers that you can teach an old dog new tricks
After Novell's super-comprehensive Zenworks package with its multiple modules and many CDs, Lansurveyor 9.5 - on a single CD - comes as a breath of fresh air.
Not only is it simple to install, but once up and running it's extremely easy to use and we had mapped out our test network within minutes of the product asking us which segment we wanted to scan. The software does this via Ping, Netbios and SNMP requests.
This latest version of the product boasts support for CDP and LLDP Discovery Protocols (Cisco Discovery Protocol and Link Layer Discovery Protocol) as well as Microsoft Baseline Security Analyzer 2.0 .
The product is organised into three components or modules. The first and principal constituent is the main console, which gives an overview of how devices and nodes on the network infrastructure are mapped out. Once we had scanned our test system we were able to drill down on specific parts of the network and unearth information on each node. The network map can by saved as a Visio or JPEG file as well.
The second module is the so-called Neon Responder - an optional component, installed on the systems that need to be monitored, that draws detailed information on a device's hardware and software and records it to a Microsoft SQL Server or MSDE database. This remote deployment tool has to be installed onto Windows or Mac OS X client machines in order to unearth this information about the computer.
The third component, Continuous Scan, acts as an intrusion detection system. Using the baseline map of the network it scans for changes on the network (surprise, surprise) on a continuous basis. This means that rogue devices, such as wireless access points installed by users, can be barred from connection to the network until they are placed on a white list and allowed access. This is achieved in conjunction with managed switches on the network and is a reasonably cheap way for small companies to include endpoint security within their infrastructure.
In addition to all of the above there's also a polling feature thrown in. This will scan critical ports on target machines and alert the administrator when an application stops responding (such as a web, mail or DNS server). We tested it by setting it to monitor a remote server which we set to go offline after five minutes. As expected the product duly notified us that the remote server could no longer be contacted.
Sign up today and you will receive a free copy of our Future Focus 2025 report - the leading guidance on AI, cybersecurity and other IT challenges as per 700+ senior executives
Verdict
Rene Millman is a freelance writer and broadcaster who covers cybersecurity, AI, IoT, and the cloud. He also works as a contributing analyst at GigaOm and has previously worked as an analyst for Gartner covering the infrastructure market. He has made numerous television appearances to give his views and expertise on technology trends and companies that affect and shape our lives. You can follow Rene Millman on Twitter.
-
 Can the ‘microshifting’ trend work in the tech sector?
Can the ‘microshifting’ trend work in the tech sector?In-depth Research shows that employees want to break up their working days into short, flexible blocks – here’s how tech leaders can implement what’s being coined as ‘microshifting’
-
 Brother DCP-L1640W review
Brother DCP-L1640W reviewReviews This compact mono laser multifunction looks perfect for home workers, but is its appeal more than skin-deep?
-
 BT to slash 55k jobs by 2030 in “brutal” cost-saving plan
BT to slash 55k jobs by 2030 in “brutal” cost-saving planNews The telco aims to become more lightweight through layoffs and digitization
-
 IDC: The business value of IBM Maximo
IDC: The business value of IBM MaximoWhitepaper Integral to the transformation of asset management
-
 Rogers Communication to invest C$10 billion in AI, oversight following outage
Rogers Communication to invest C$10 billion in AI, oversight following outageNews Canadian telco giant has promised internal transformation after a network-wide blackout caused major disruption in Canada earlier this month
-
 How to choose APM software for your business
How to choose APM software for your businessWhitepaper A market guide to Asset Management Performance software
-
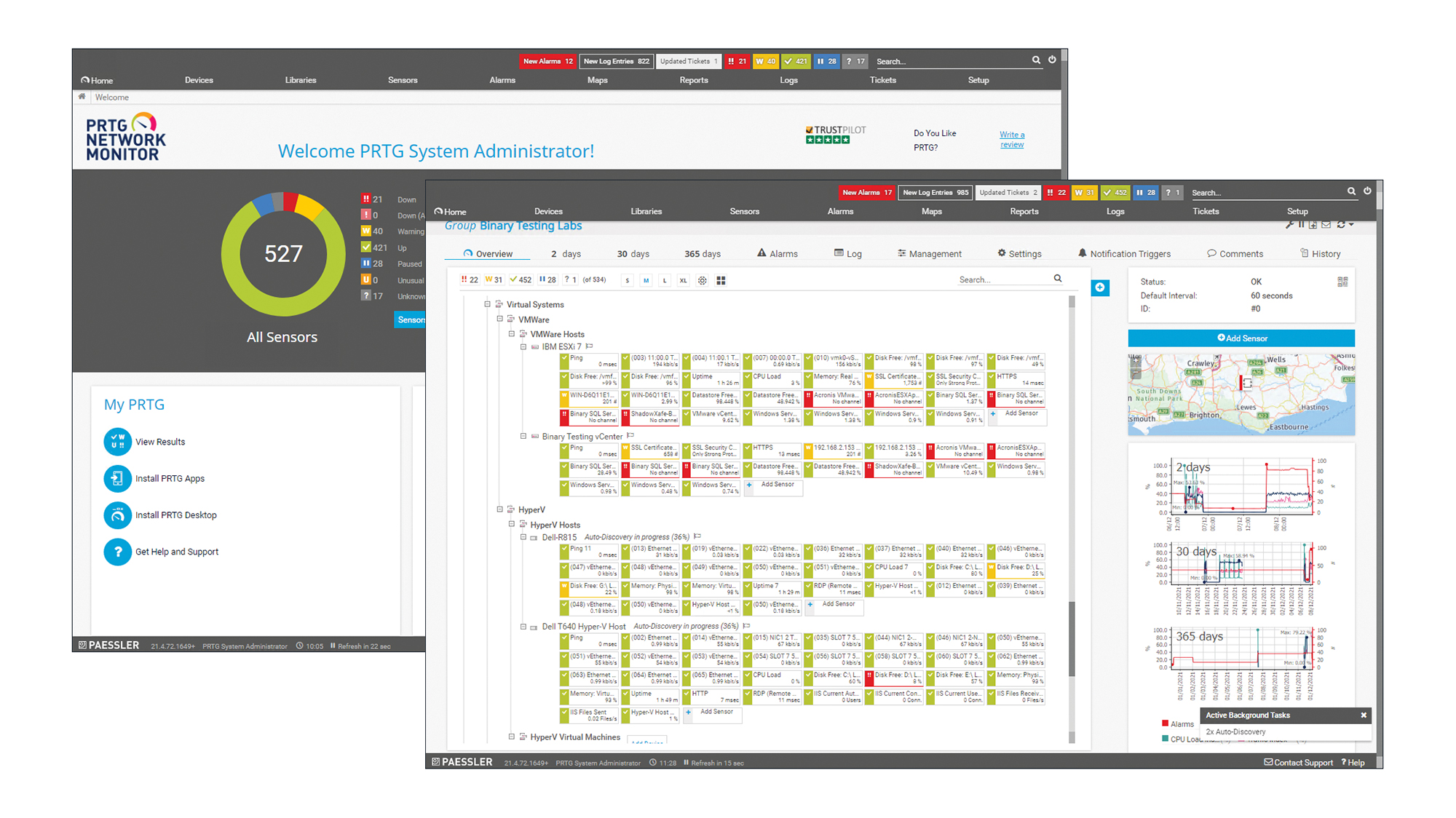
 Paessler PRTG Network Monitor 21.4 review: Hard to beat
Paessler PRTG Network Monitor 21.4 review: Hard to beatReviews This affordable and versatile monitoring solution suits all types of networks with a sensor for every occasion
-
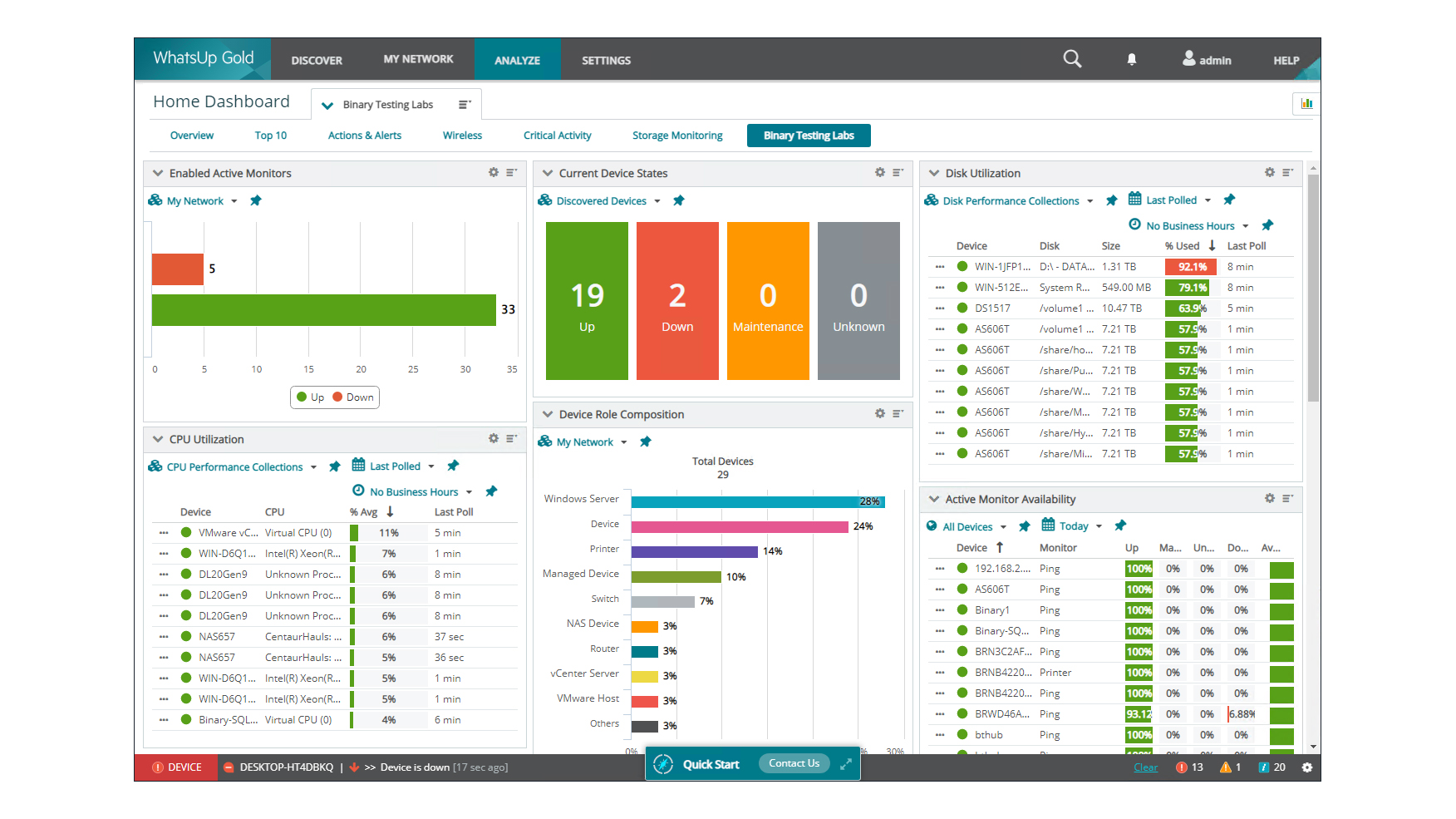
 Progress Software WhatsUp Gold 2021.1 review: More powerful than ever
Progress Software WhatsUp Gold 2021.1 review: More powerful than everReviews Add-ons increase the price, but WhatsUp Gold is easy to use and provides a superb range of monitoring tools
-
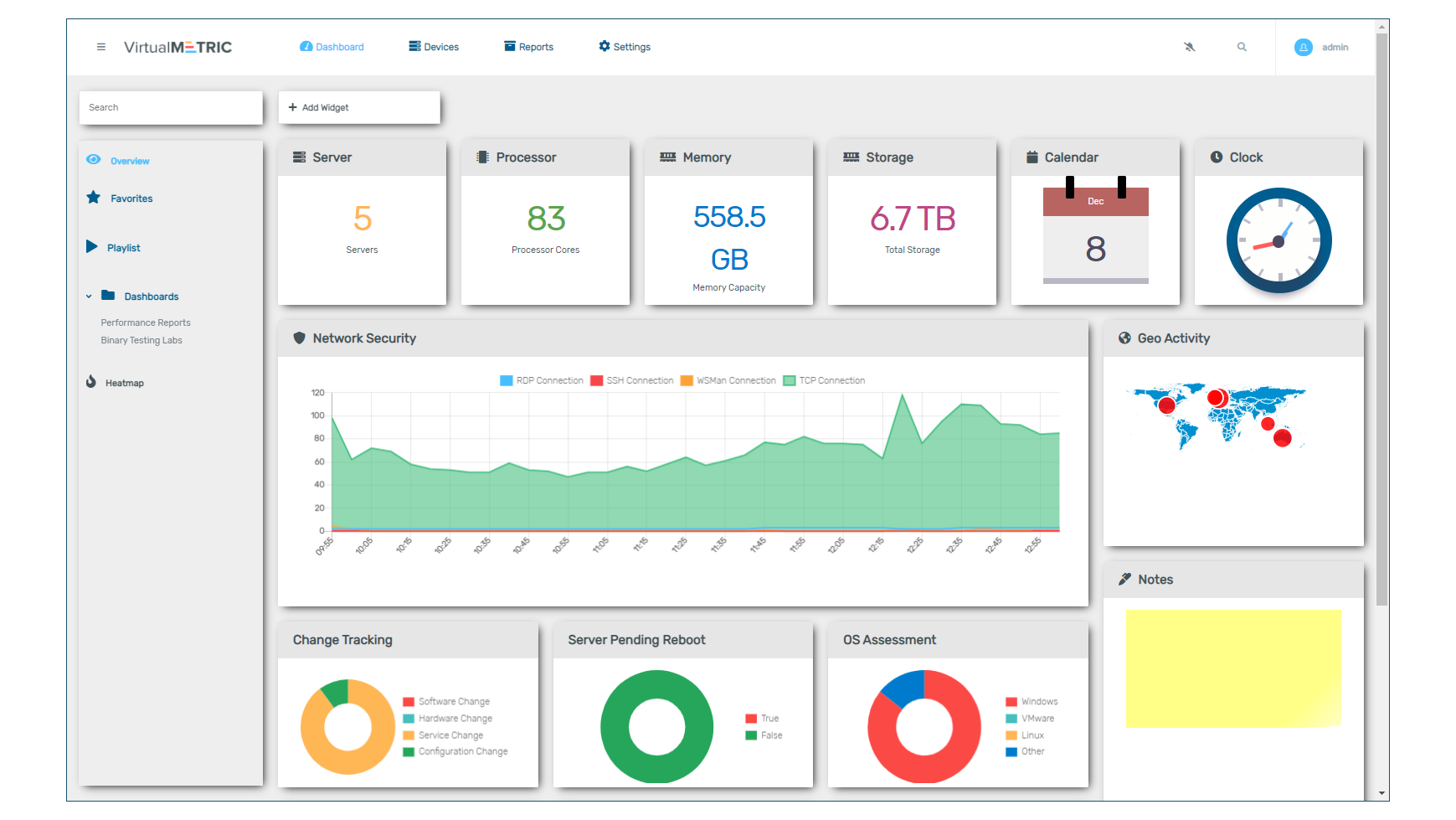 VirtualMetric review: Let down by poor support
VirtualMetric review: Let down by poor supportReviews This server-focused solution exposes a remarkable amount of information, but its flaws are hard to overlook
-
 Achieving network modernisation for the decade ahead
Achieving network modernisation for the decade aheadWhitepaper An IDC whitepaper


