Network management software
Rene Millman delves into the world of network management software and discovers that you can teach an old dog new tricks
With thousands of desktops and hundreds of servers to look after, systems administrators need tools to look after all of them. Nowadays it is not enough that PCs have all the relevant software on them to allow employees to do their jobs. There is also the question of making sure that those computers are up-to-date with the latest security patches, so that they don't become an entry point into the infrastructure from hackers or use up valuable bandwidth sending out spam from a compromised computer.
But in such a vast and complex environment how on earth do you keep on top of it all? The answer is network management software. These tools are the software equivalent of the Swiss army knife. They help you keep on top of everything from security patches to licensing and asset management. They'll tell you if that extra copy of Office you're paying for is actually being used. They can help you manage the health and security of the network, making sure that bandwidth was used properly and rogue devices were barred from the network.
They're the ultimate network reference tool, essential for keeping tabs on the network infrastructure and what's going on in it. But what exactly makes good network management software? We took a look at six of the more popular products to find out...
There are several different aspects to consider when looking at network management software. While asset management can tell you what is infrastructure holds, good products should be able to trawl up information right down to the speed of the processor and the amount of memory as well as any applications running on a single desktop PC. We also scored any products that flagged up rogue applications that were installed on endpoints that were outside of our test policy.
Some products provide remote control facilities for helpdesk staff, so we evaluated this aspect too. Agents installed on desktops should not take up too many resources and also should not allow the computer to become compromised. We scored products on how well the agents performed both by how many functions they undertook and how fast they completed those functions.
Lastly, we looked at the reporting functions of all the products. The products that did best presented usable information that could easily form part of a CIO's digital dashboard giving them as complete a view of the network and the devices connected to it as possible.
Testing
Sign up today and you will receive a free copy of our Future Focus 2025 report - the leading guidance on AI, cybersecurity and other IT challenges as per 700+ senior executives
To test the tools, we set up a test bed of a typical heterogeneous environment comprising Windows Servers (we chose Windows Server 2003 as the main server OS for the purposes of this test), Linux Servers (Red Hat Enterprise Server 4) and some Windows (SP1 and SP2) and Macintosh desktops (running the latest version of OS X). We also had some laptops and even a PDA for good measure. The network was run over a managed switch and connected to that was a Netgear wireless access point to which the laptop was connected.
Rene Millman is a freelance writer and broadcaster who covers cybersecurity, AI, IoT, and the cloud. He also works as a contributing analyst at GigaOm and has previously worked as an analyst for Gartner covering the infrastructure market. He has made numerous television appearances to give his views and expertise on technology trends and companies that affect and shape our lives. You can follow Rene Millman on Twitter.
-
 IDC: The business value of IBM Maximo
IDC: The business value of IBM MaximoWhitepaper Integral to the transformation of asset management
-
 BT to slash 55k jobs by 2030 in “brutal” cost-saving plan
BT to slash 55k jobs by 2030 in “brutal” cost-saving planNews The telco aims to become more lightweight through layoffs and digitization
-
 Rogers Communication to invest C$10 billion in AI, oversight following outage
Rogers Communication to invest C$10 billion in AI, oversight following outageNews Canadian telco giant has promised internal transformation after a network-wide blackout caused major disruption in Canada earlier this month
-
 How to choose APM software for your business
How to choose APM software for your businessWhitepaper A market guide to Asset Management Performance software
-
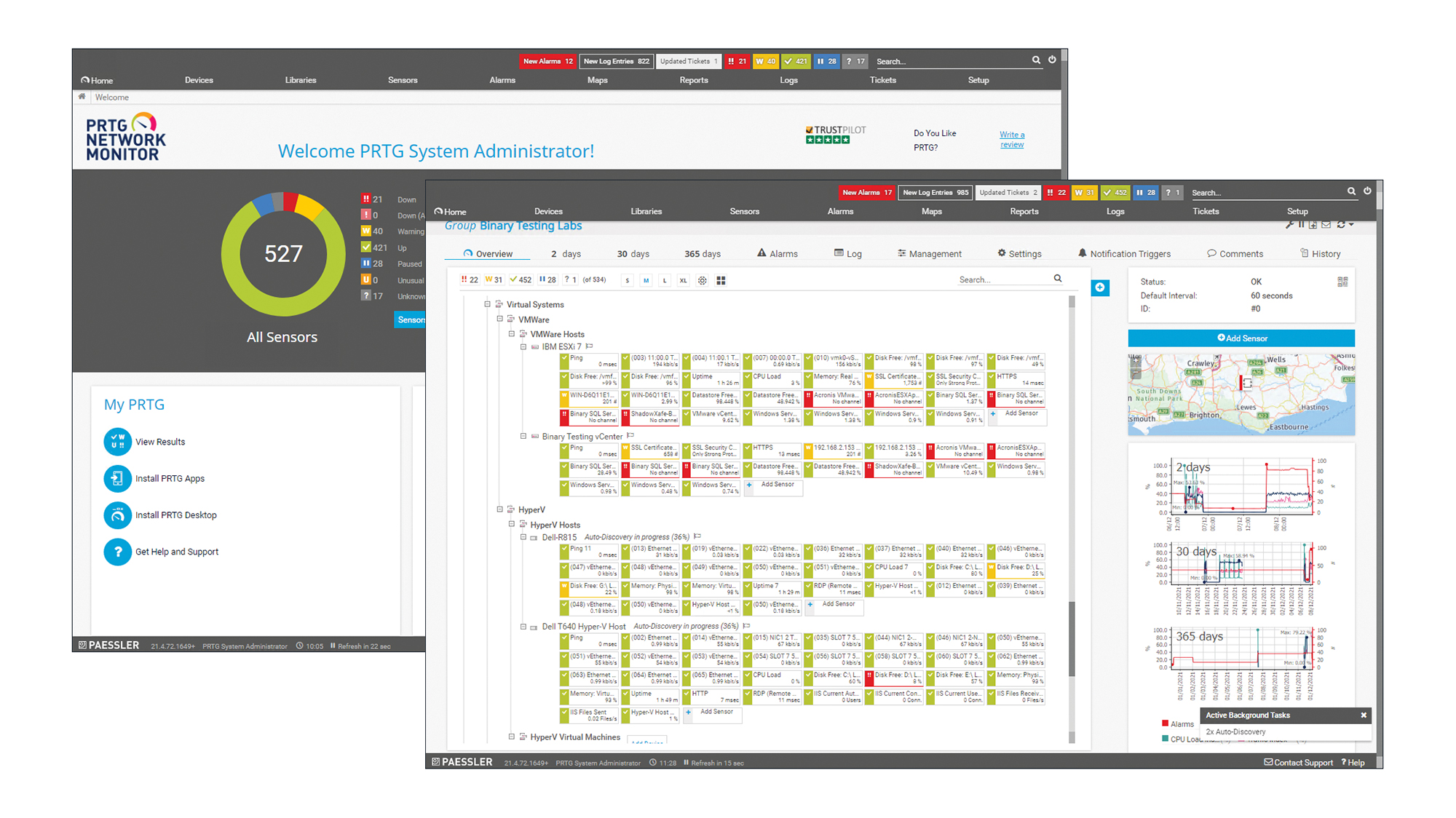
 Paessler PRTG Network Monitor 21.4 review: Hard to beat
Paessler PRTG Network Monitor 21.4 review: Hard to beatReviews This affordable and versatile monitoring solution suits all types of networks with a sensor for every occasion
-
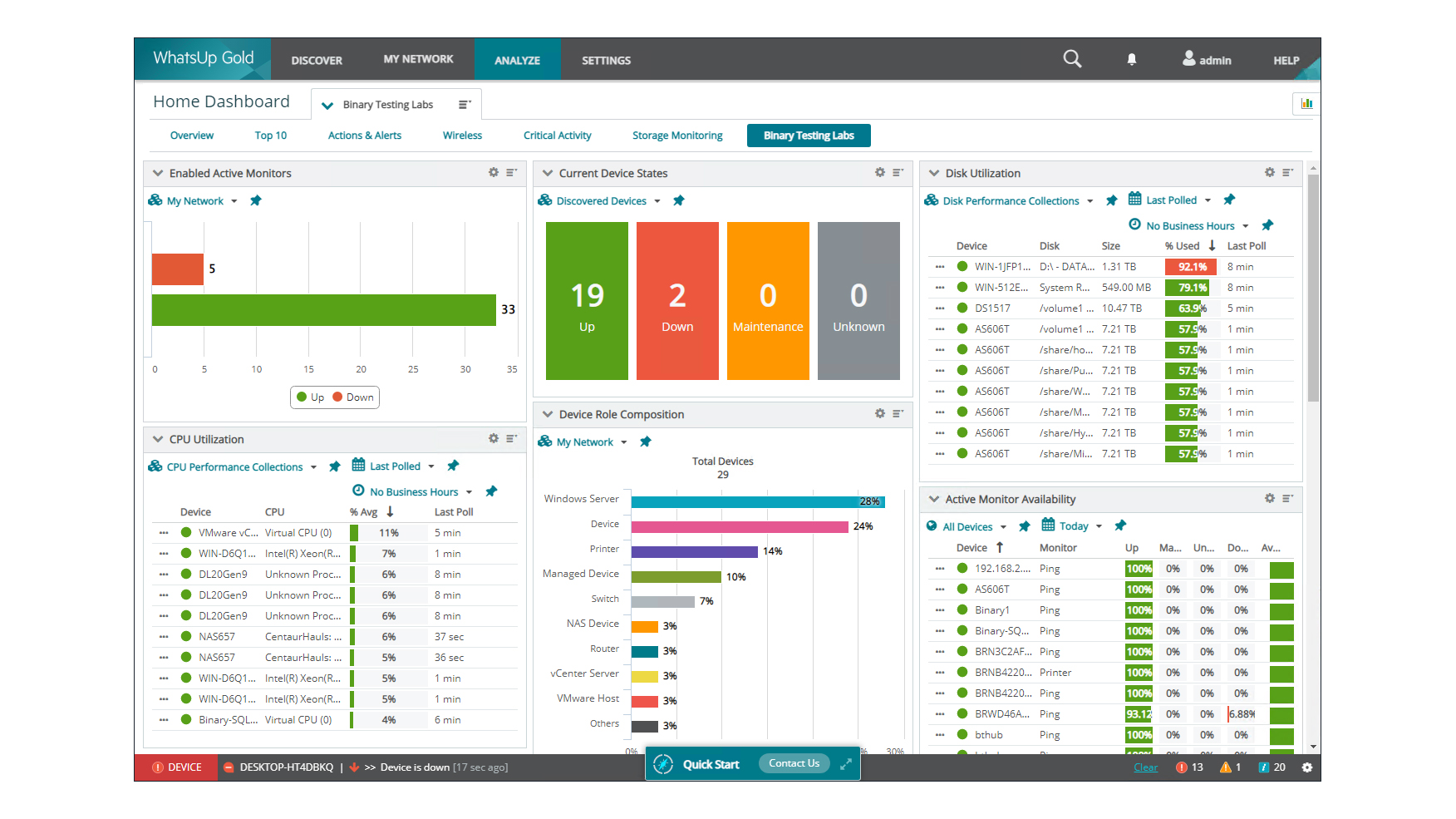
 Progress Software WhatsUp Gold 2021.1 review: More powerful than ever
Progress Software WhatsUp Gold 2021.1 review: More powerful than everReviews Add-ons increase the price, but WhatsUp Gold is easy to use and provides a superb range of monitoring tools
-
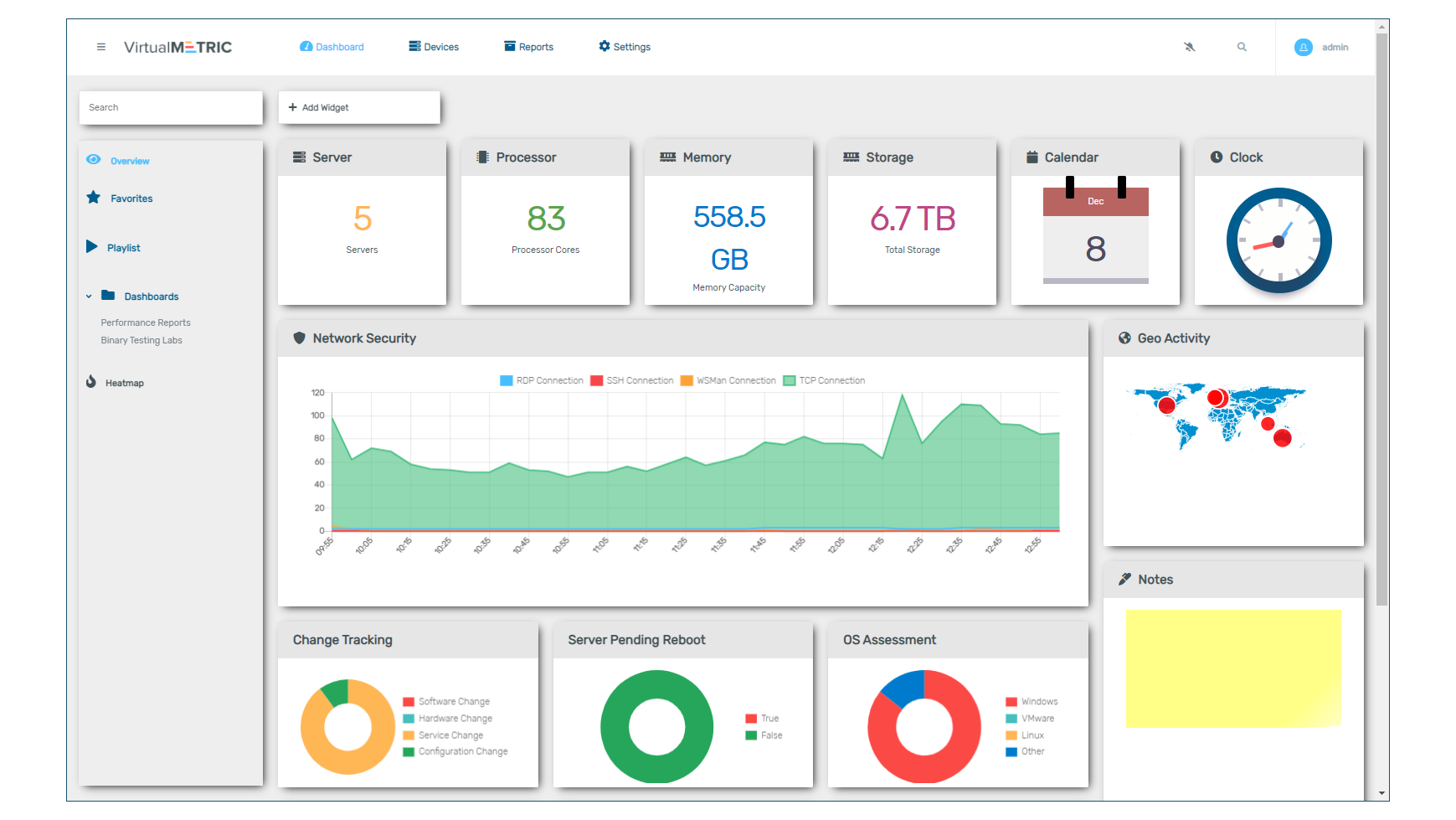 VirtualMetric review: Let down by poor support
VirtualMetric review: Let down by poor supportReviews This server-focused solution exposes a remarkable amount of information, but its flaws are hard to overlook
-
 Achieving network modernisation for the decade ahead
Achieving network modernisation for the decade aheadWhitepaper An IDC whitepaper




