BlackBerry Persona Desktop delivers zero-trust security at the endpoint
New security solution learns user behavior and can take action if there’s an abnormality
Sign up today and you will receive a free copy of our Future Focus 2025 report - the leading guidance on AI, cybersecurity and other IT challenges as per 700+ senior executives
You are now subscribed
Your newsletter sign-up was successful
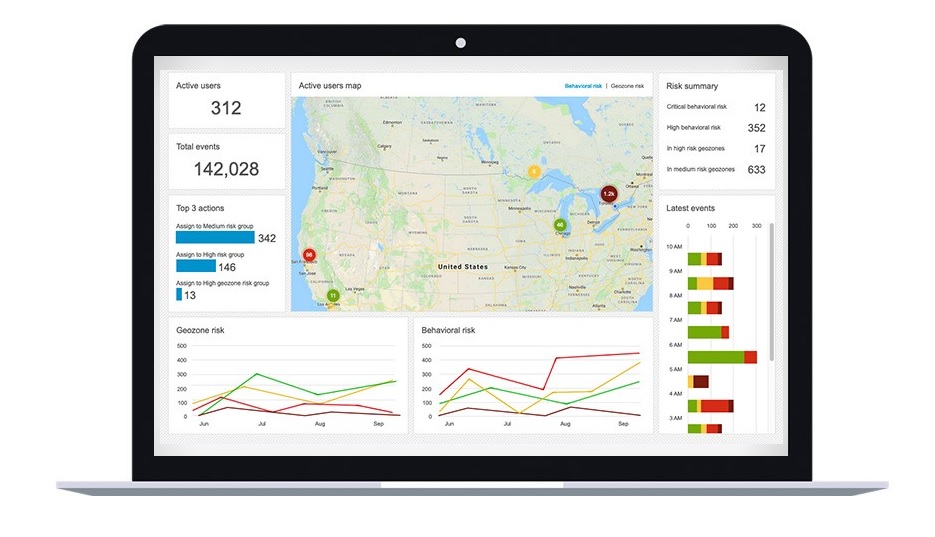
BlackBerry has announced BlackBerry Persona Desktop, an all-new security solution that uses advanced artificial intelligence (AI) and machine learning to detect user and entity behavior abnormalities.
Once the new BlackBerry Persona Desktop notices an irregularity in behavior, it protects the endpoint, network and data.
BlackBerry Persona Desktop works at the endpoint, eliminating the need to share data back to the cloud before acting. This allows it to work in real-time with minimal delay to prevent hacks and data breaches.
On top of working faster, BlackBerry Persona Desktop also protects against even the most challenging security challenges, including:
- Stolen credentials: Persona Desktop protects in the event of stolen credentials by learning how a user works and their interaction with a device. If Persona Desktop senses abnormal interaction, it sends an alert through the cloud and takes other threat-mitigation actions, like asking for second-factor authentication.
- Insider threats: If a rogue employee attempts to breach your system, the Persona Desktop can detect the abnormal behavior and flag the risk. It’ll then alert the administrator, who determines what action Persona Desktop takes to mitigate the threat.
- Physical compromise: If someone physically compromises or steals a device, BlackBerry Persona Desktop uses biometric capabilities, including keystrokes and mouse movement, to sense a different user and alert an administrator or lock the user out.
BlackBerry Personal is available with the BlackBerry Cyber Suite, which is a unique combination of endpoint protection (EPP), mobile threat defense (MTD), endpoint detection and response (EDR), and user and entity behavior analytics (UEBA) products together in one package.
Sign up today and you will receive a free copy of our Future Focus 2025 report - the leading guidance on AI, cybersecurity and other IT challenges as per 700+ senior executives
-
 AWS CEO Matt Garman isn’t convinced AI spells the end of the software industry
AWS CEO Matt Garman isn’t convinced AI spells the end of the software industryNews Software stocks have taken a beating in recent weeks, but AWS CEO Matt Garman has joined Nvidia's Jensen Huang and Databricks CEO Ali Ghodsi in pouring cold water on the AI-fueled hysteria.
-
 Deepfake business risks are growing
Deepfake business risks are growingIn-depth As the risk of being targeted by deepfakes increases, what should businesses be looking out for?
-
 Windows 11 Pro and CDW - Overcoming today's escalating cyberthreats
Windows 11 Pro and CDW - Overcoming today's escalating cyberthreatswhitepaper Employing a security-by-default approach with the latest Windows 11 Pro devices
-
 Onward: How security drives business opportunity
Onward: How security drives business opportunitywhitepaper Do you consider security as a business investment or a business enabler?
-
 Blackberry revenue falls by 4% as cyber security division takes hit
Blackberry revenue falls by 4% as cyber security division takes hitNews Despite this, the company’s Internet of Things (IoT) division increased its revenue by 28% as it attracted new customers from the automotive sector
-
 BlackBerry revival is officially dead as OnwardMobility shuts down
BlackBerry revival is officially dead as OnwardMobility shuts downNews The Texas-based startup is mysteriously shutting down and taking its ultra-secure 5G BlackBerry with it
-
 BlackBerry and AWS are developing a standardized vehicle data platform
BlackBerry and AWS are developing a standardized vehicle data platformNews Platform will give automakers a standardized way to process data from vehicle sensors in the cloud
-
 BlackBerry thwarts mobile phishing attacks with new AI tools
BlackBerry thwarts mobile phishing attacks with new AI toolsNews The company's Protect Mobile platform alerts users to potential malware before a link is clicked
-
 Apple's T2 security chip has an "unpatchable" vulnerability
Apple's T2 security chip has an "unpatchable" vulnerabilityNews Exploiting the checkm8 and blackbird flaws can grant attackers control over a macOS-powered device
-
 A 5G BlackBerry phone with physical keyboard is coming in 2021
A 5G BlackBerry phone with physical keyboard is coming in 2021News The business phone to be resurrected with OnwardMobility and FIH Mobile planning a security-savvy enterprise handset