Burp Suite review: A highly functional tool your business should learn about
This venerable web application security tool is so much more than a simple proxy

-
+
Comes in a free version with lots of functionality
-
+
Extensive free educational resources
-
+
Lots of community plug-ins
-
-
Paid versions aren't cheap
- -

Burp Suite is a well-established tool kit for ethical hackers, including web developers who want to harden their programs. Originally created as a bare-bones intrusion tool in 2003, it has since become a robust web application security analysis framework, including features such as a proxy, a logger, and a custom intrusion tool. Sadly, the best feature of the original incarnation – burping sounds that the user couldn't turn off – is no longer a thing.
READ MORE
The service now comes in three editions: Community, which is a free version targeting casual users, Professional, for more serious practitioners, and Enterprise, which focuses on larger organizations with collaborative application security and development teams.
We looked at both the Community and Professional editions to get a sense of their functionality and what was different. For many, the Community edition of Burp Suite will be more than adequate. The biggest feature that it lacks is persistence because users cannot save website investigation projects to disk. That makes it less practical than the Pro version for collaboration, or even for longer-term investigations that a researcher might want to come back to. Still, it's useful for poking around your own applications, or other people's with permission.
Burp Suite: Proxy setup
The proxy is the heart of Burp Suite, sitting between your browser and the website you're analyzing, intercepting traffic, and allowing you to read and change it. You can either use a browser proxy plug-in for Burp Suite to control, or you can use Burp Suite's tightly integrated built-in Chromium-based browser.
The proxy enables you to intercept and change both requests made to the site and responses to those requests. You can filter which domains are intercepted using the Target menu, which shows you everything about the target site including a site map. This is one of many function areas demonstrating just how comprehensive the tool has become, and it sits alongside many other menu-based functions in the program. Here's an empty initial view of the Pro version's Dashboard view, which shows various summaries of Burp Suite activity.
The proxy menu allows you to set rules for what kinds of traffic are intercepted, along with what to do with them. You can also change requests on the fly. An HTTP history section in this section shows you your requests, allowing you to drill down into the request and response bodies. You can make individual notes on these requests and also highlight them in different colors for easy categorization, although remember that only the Pro version allows you to save such details for posterity.
Burp Suite: Requests
You can send requests directly from the HTTP history section to other areas of Burp Suite. One of these is the repeater, which allows you to repeatedly tinker with requests and resend them to assess the results. This is useful if you want to tinker with an input parameter a couple of times to see if an SQL injection attack might work. You can send multiple requests to the repeater, each of which goes into a tab that you can rename. That's handy for identifying and recording interesting finds.
Sign up today and you will receive a free copy of our Future Focus 2025 report - the leading guidance on AI, cybersecurity and other IT challenges as per 700+ senior executives
What if you want to run a larger set of requests, perhaps testing user name inputs to test what responses the site sends back? That's where the intruder function comes in. It's an area to mount attacks against websites by specifying parts of a request as placeholders to insert different text. For example, you might want to highlight the someuser part of https://www.anexamplecompany.com/login.php?user=someuser&password=somepassword as a placeholder, replacing it with entries from a word list, and then bombarding the site with results. You can set match strings to look for in the site responses, and you can also use another function, the Comparer, to highlight what changed.
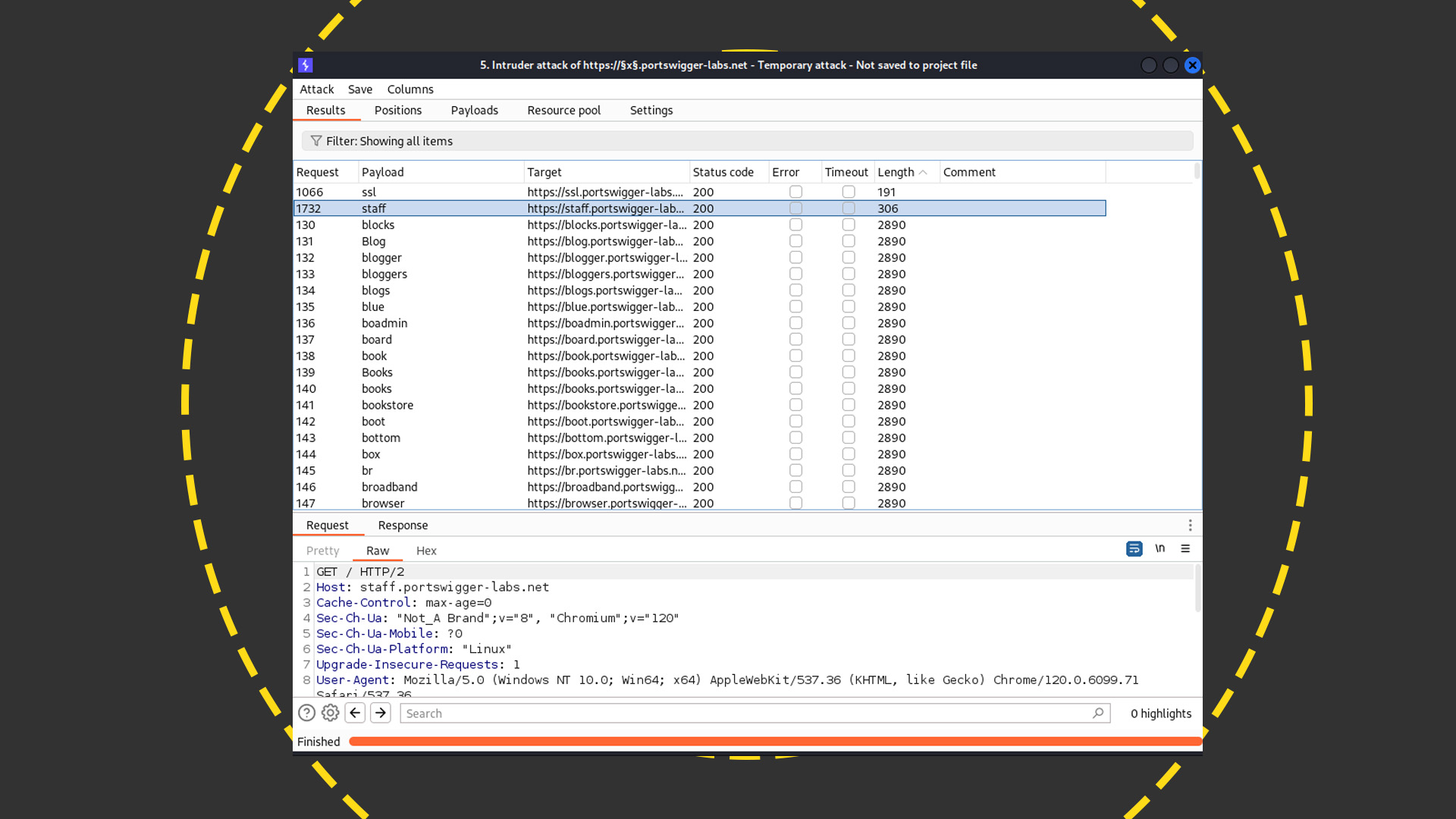
Another trick with the Intruder section is to look for subdomains under your target domain by specifying a placeholder and then running automated requests that replace that field with words from a list. Then you can analyze the results. For example, sorting all the responses to queries in this subdomain list that returned a 200 header revealed a staff subdomain that was shorter in length than the others. This turned out to be a login form, which would warrant further analysis.
Burp Suite: Professional version
Aside from allowing you to save your project to disk, there are some other features in the Pro edition that range from convenient to extremely useful. At the convenient-but-not-crucial end of the spectrum is the inclusion of built-in word lists covering things like user names and domains for Intruder. You could easily find such things online and load them or simply paste them into the relevant area yourself, but pre-baked options make it slightly easier and speed up your job as a practitioner.
The Pro version also comes with some extra tools that make it easier to enumerate sites, or to understand what you've already mapped. These include a Discover Content option that uses common word lists to search a site for hidden directories and other assets, along with subdomains that aren't linked directly from the website. This is a good way to discover development and testing domains not meant to be exposed to the public.
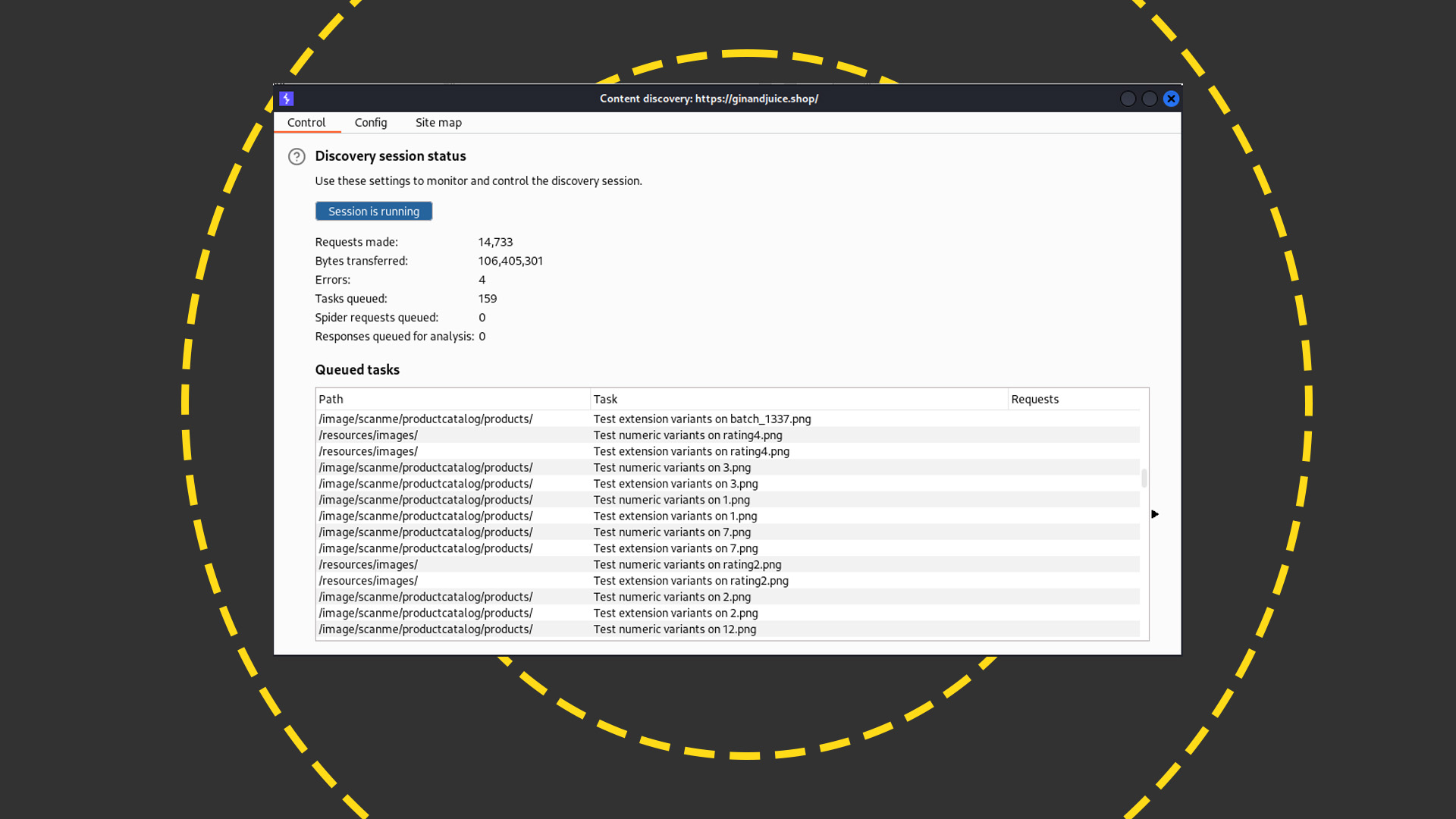
Be warned, though; even with another advantage of the Pro version – threaded operation for faster site hammering – this can take a while. Some tasks such as the subdomain search we mentioned might even be best left running overnight.
You can also use the Analyze Target function in the Pro version to report every parameter used in a mapped site and which URLs they are found at:
<target-analyzer.png>
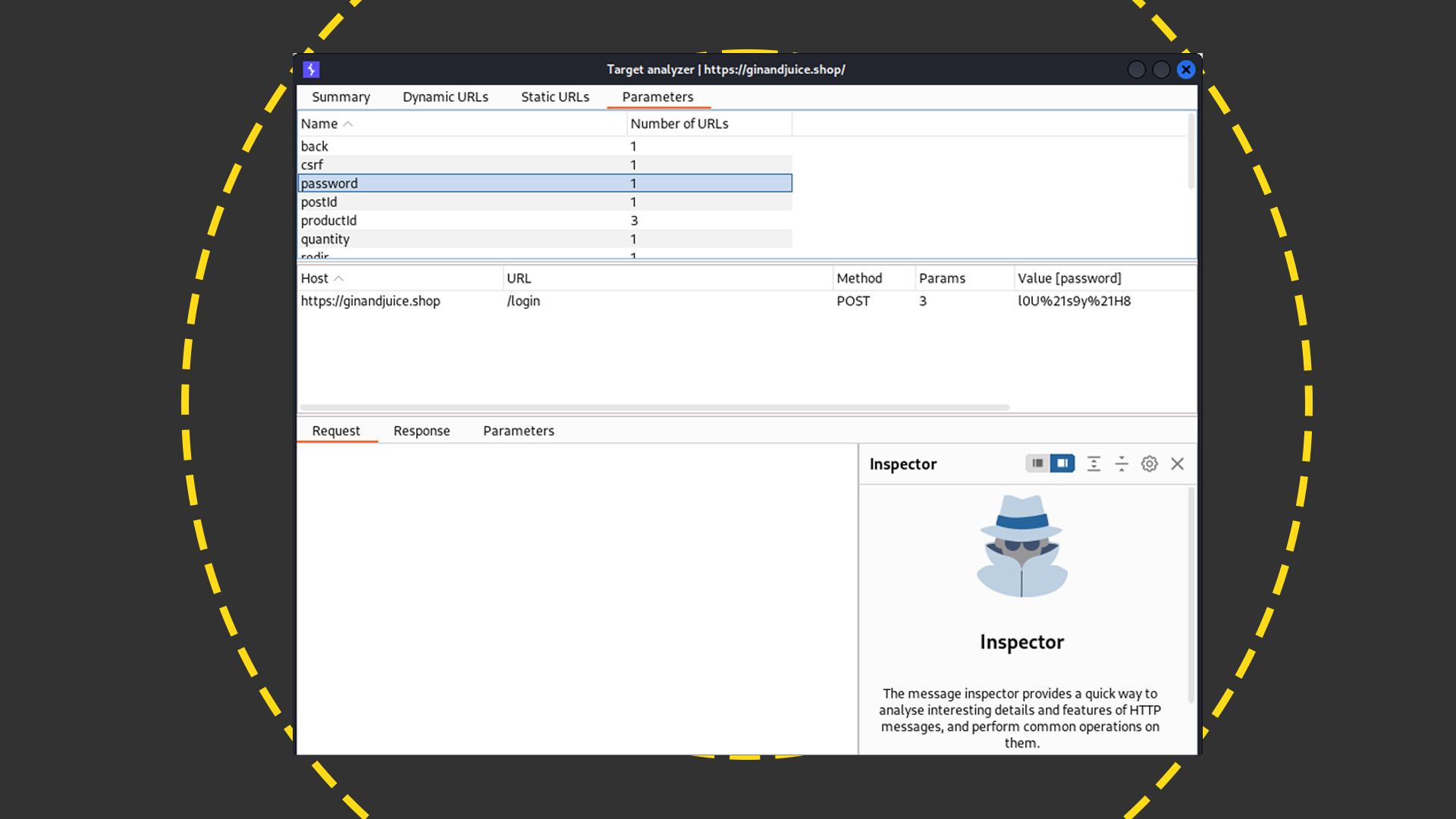
At the extremely useful end of the spectrum is the Pro version's scanning and auditing feature. This enables you to point Burp Suite at a website and launch vulnerability scans ranging from a simple passive check to an aggressive bout of intense door-rattling. You can then highlight the issues in the site and drill down into each of them, like so.
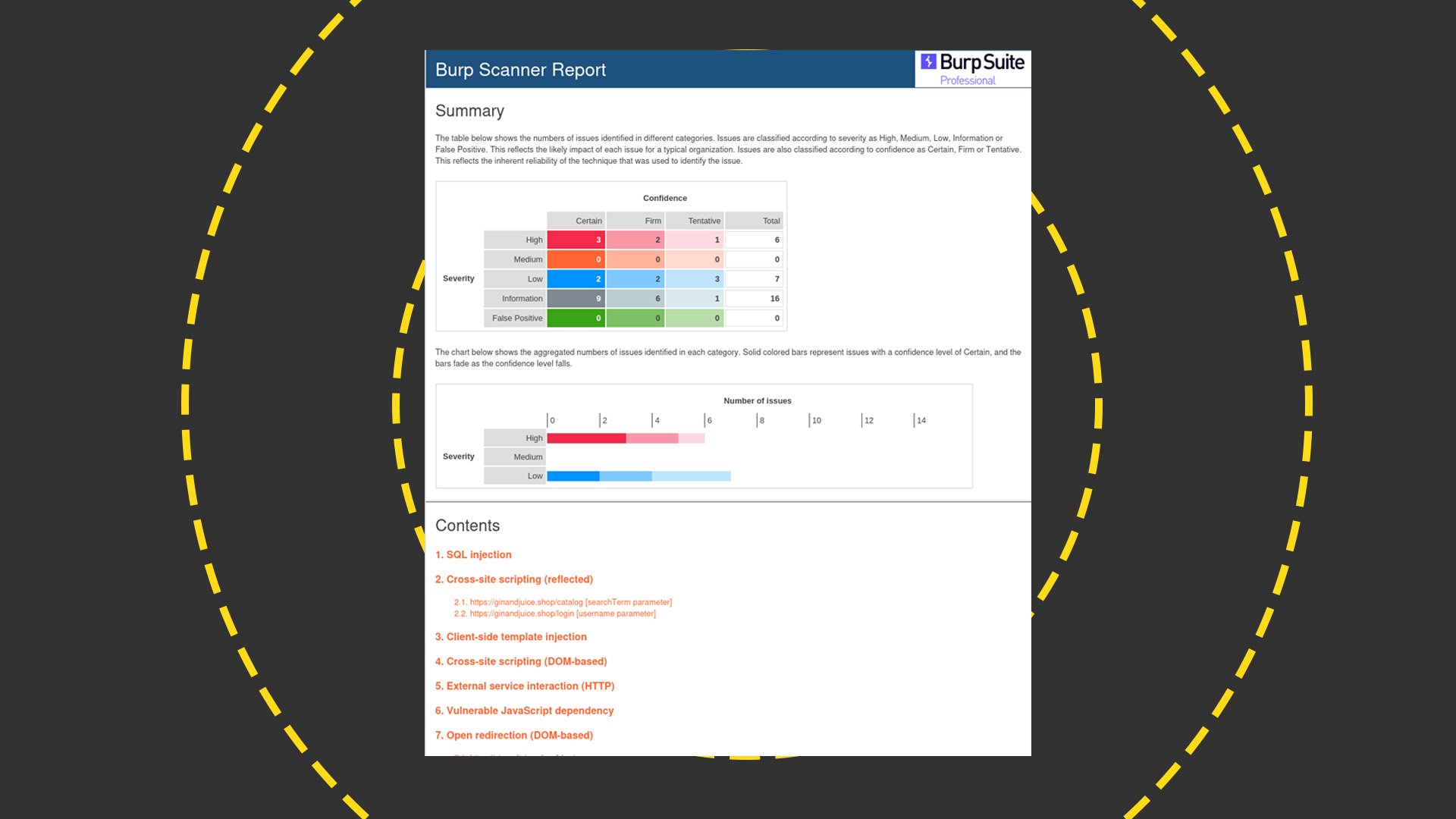
The Pro version also lets you produce customizable HTML reports for distribution to your team. That's handy if you're a compliance or security professional who needs to compile a list of things for a developer to address.
Burp Suite: Apps and plugins
There are plenty of other goodies in Burp Suite. For example, it handles WebSockets and also includes some more esoteric goodies like the Sequencer. This analyzes multiple strings to see how random they are, which you can use to see whether, say, session tokens or CSRF tokens are predictable and therefore a security issue.
RELATED RESOURCE

What do CEOs need to know about AI?
DOWNLOAD NOW
Burp Suite is a highly functional tool that you can get a lot out of when you understand how to use it properly. It gets even deeper when you delve into the many plugins that the community has developed for this extensive product.
One of the best parts about the whole experience is the set of education resources that Portswigger has created for Burp Suite users. There is an online academy, complete with labs that you can access to solve challenges with Burp Suite. The site tracks how many of these bite-sized exercises you've completed, noting when you've progressed to more advanced levels so that you can tackle tougher tasks. There are also plenty of instructional videos to watch, and even intentionally vulnerable websites to target for practice. This all effectively turns the academy into a beefy ethical hacking course. It's a great way to build a bigger community around an already well-established and respected product.
As with all ethical hacking tools, you can use Burp Suite for good or evil, but we hope you use it for the former. If you're a web developer, it pays to spend time learning this product so that you can spot and seal off a range of vulnerabilities in your application. Making the effort during development could save you some embarrassing incidents in production.
Danny Bradbury has been a print journalist specialising in technology since 1989 and a freelance writer since 1994. He has written for national publications on both sides of the Atlantic and has won awards for his investigative cybersecurity journalism work and his arts and culture writing.
Danny writes about many different technology issues for audiences ranging from consumers through to software developers and CIOs. He also ghostwrites articles for many C-suite business executives in the technology sector and has worked as a presenter for multiple webinars and podcasts.
-
 Hackers are using LLMs to generate malicious JavaScript in real time – and they’re going after web browsers
Hackers are using LLMs to generate malicious JavaScript in real time – and they’re going after web browsersNews Defenders advised to use runtime behavioral analysis to detect and block malicious activity at the point of execution, directly within the browser
By Emma Woollacott Published
-
 AI coding is taking off in the US – but developers in another country are “catching up fast”
AI coding is taking off in the US – but developers in another country are “catching up fast”News Developers in the United States are leading the world in AI coding practices, at least for now
By Nicole Kobie Published
-
 Veeam ramps up growth plans with trio of leadership hires
Veeam ramps up growth plans with trio of leadership hiresNews The data resilience vendor has reshaped its senior leadership team to deepen partner engagement and streamline customer success in the AI era
By Daniel Todd Published
