Sophos Intercept X Advanced review: A huge range of endpoint protection measures for the price
A superb range of security measures and a well-designed cloud portal make endpoint protection a breeze
-
+
Huge range of policy customisation options
-
+
Smart AI features
-
+
Straightforward management
-
-
None

Sophos offers an impressive portfolio of security services and, as an early adopter of cloud management, it's ensured everything can be accessed from its Central administrative portal. Along with the Intercept X Advanced workstation and server endpoint protection on review, you can use Central to look after Sophos' Mobile threat defense package along with its XGS firewalls, Wi-Fi 6/6E access points, 100 and 200 series network switches, and zero trust network access service.
READ MORE

That's a lot to pack into one management portal, but Sophos has done a fine job of keeping it simple. The main dashboard provides an overview of your company's security posture, and all endpoint protection services are neatly separated into three sidebar menu categories for workstations, servers, and mobiles.
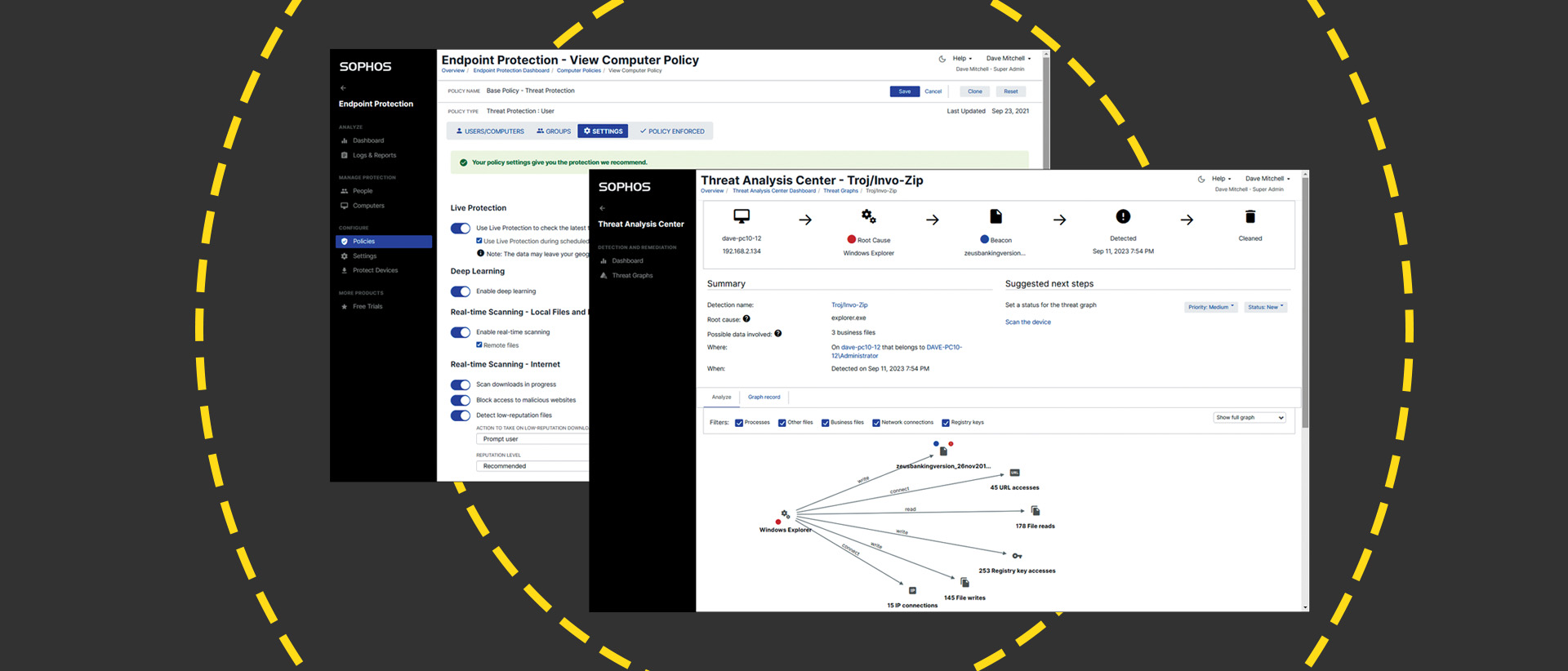
Along with essential malware and threat protection services, Intercept X Advanced supports multiple security policies plus application and device controls. It employs AI-based deep learning to defend against unknown malware, blocks ransomware attacks using behavioral analysis and enables a threat analysis center.
An XDR (extended detection and response) license allows you to create your own custom threat cases. This provides deeper malware analysis and threat intelligence, on-demand endpoint isolation, and suspicious event detection and prioritization to identify targeted attacks.
Sophos Intercept X Advanced: Setup
Deployment is swift. You place the Windows and macOS installers in a central distribution point or create users in the portal and email a link to them. A different agent is used for Windows servers but, in both cases, they only take ten minutes to install, connect to your portal account and retrieve a base security policy.
The base threat protection policy has all recommended security settings enabled and is always applied to users and devices if no other policy has been assigned. Other policies are provided for web, application, Windows firewall and device controls, and data loss prevention, although these are deactivated and require configuration and assignment. Policies present an extensive range of security measures and include CryptoGuard ransomware protection.
RELATED RESOURCE

Learn about the three scenarios commonly encountered by end users that pose difficulties for network operations teams
When any file is opened for writing, it places a temporary clean copy in a proprietary cache on the local drive and, if it detects malicious encryption activity, it will automatically roll back the file to its original state.
Sign up today and you will receive a free copy of our Future Focus 2025 report - the leading guidance on AI, cybersecurity and other IT challenges as per 700+ senior executives
Custom policies are easily created by cloning the preconfigured ones and tweaking their settings to suit. These can be assigned to device groups, and if you import users via the free Active Directory (AD) sync tool or Azure sync service, you can apply policies to users so they're always protected no matter what device they have signed in to.
Sophos cuts through alert smokescreens as only unresolved events that need your attention to appear in the Central dashboard and cause email notifications to be issued. We used our malware collection to create a virus outbreak condition on one PC which was highlighted immediately, whereas other events such as successful malware removals and website blocks were only posted in the logs and reports section.
The portal's threat analysis center provides a basic dashboard showing the most recent threats. Selecting one provides a full analysis of events and a one-click option to clean up all associated files and Registry entries and block them so other devices can't run it. Sophos has also added a new XDR threat analysis center dashboard that provides smarter widget-based graphical views of malware detection.
Sophos Intercept X Advanced delivers a huge range of endpoint protection measures for the price. It's simple to deploy, device and user policies add flexibility and seamless integration with the Central cloud portal makes management simple.
This content originally appeared on ITPro's sibling magazine PC Pro. For more information and to subscribe, please visit PC Pro's subscription site.
Dave is an IT consultant and freelance journalist specialising in hands-on reviews of computer networking products covering all market sectors from small businesses to enterprises. Founder of Binary Testing Ltd – the UK’s premier independent network testing laboratory - Dave has over 45 years of experience in the IT industry.
Dave has produced many thousands of in-depth business networking product reviews from his lab which have been reproduced globally. Writing for ITPro and its sister title, PC Pro, he covers all areas of business IT infrastructure, including servers, storage, network security, data protection, cloud, infrastructure and services.
-
 CISA’s interim chief uploaded sensitive documents to a public version of ChatGPT – security experts explain why you should never do that
CISA’s interim chief uploaded sensitive documents to a public version of ChatGPT – security experts explain why you should never do thatNews The incident at CISA raises yet more concerns about the rise of ‘shadow AI’ and data protection risks
By Ross Kelly Published
-
 Former Google engineer convicted of economic espionage after stealing thousands of secret AI, supercomputing documents
Former Google engineer convicted of economic espionage after stealing thousands of secret AI, supercomputing documentsNews Linwei Ding told Chinese investors he could build a world-class supercomputer
By Emma Woollacott Published
-
 OpenAI admits 'losing access to GPT‑4o will feel frustrating' for users – the company is pushing ahead with retirement plans anway
OpenAI admits 'losing access to GPT‑4o will feel frustrating' for users – the company is pushing ahead with retirement plans anwayNews OpenAI has confirmed plans to retire its popular GPT-4o model in February, citing increased uptake of its newer GPT-5 model range.
By Ross Kelly Published
