Hackers are spoofing themselves as GitHub's Dependabot to steal user passwords
GitHub Dependabot was crudely spoofed in hundreds of successful attacks on open source projects


Sign up today and you will receive a free copy of our Future Focus 2025 report - the leading guidance on AI, cybersecurity and other IT challenges as per 700+ senior executives
You are now subscribed
Your newsletter sign-up was successful
Hundreds of GitHub repositories have been targeted by a threat actor masked as the GitHub platform’s Dependabot feature to install password-stealing malware.
The threat actor targeted website projects on GitHub and was able to threaten the security of an array of end users with a crude manipulation of their identity.
Dependabot is GitHub’s automated dependency-management tool which scans projects for security vulnerabilities and outdated versions, automatically generating pull requests with details of the automatically applied fixes.
Seeing Dependabot contributions in a GitHub project is common and there are a number of ways a genuine commit can be identified.
Dependabot has a unique blue avatar, which is displayed as a square image in commit logs. Human GitHub users’ avatars are displayed as circles. The feature also carries with it a unique ‘Bot’ tag that’s applied next to the ‘dependabot’ alias - a UI feature that a user could not replicate.
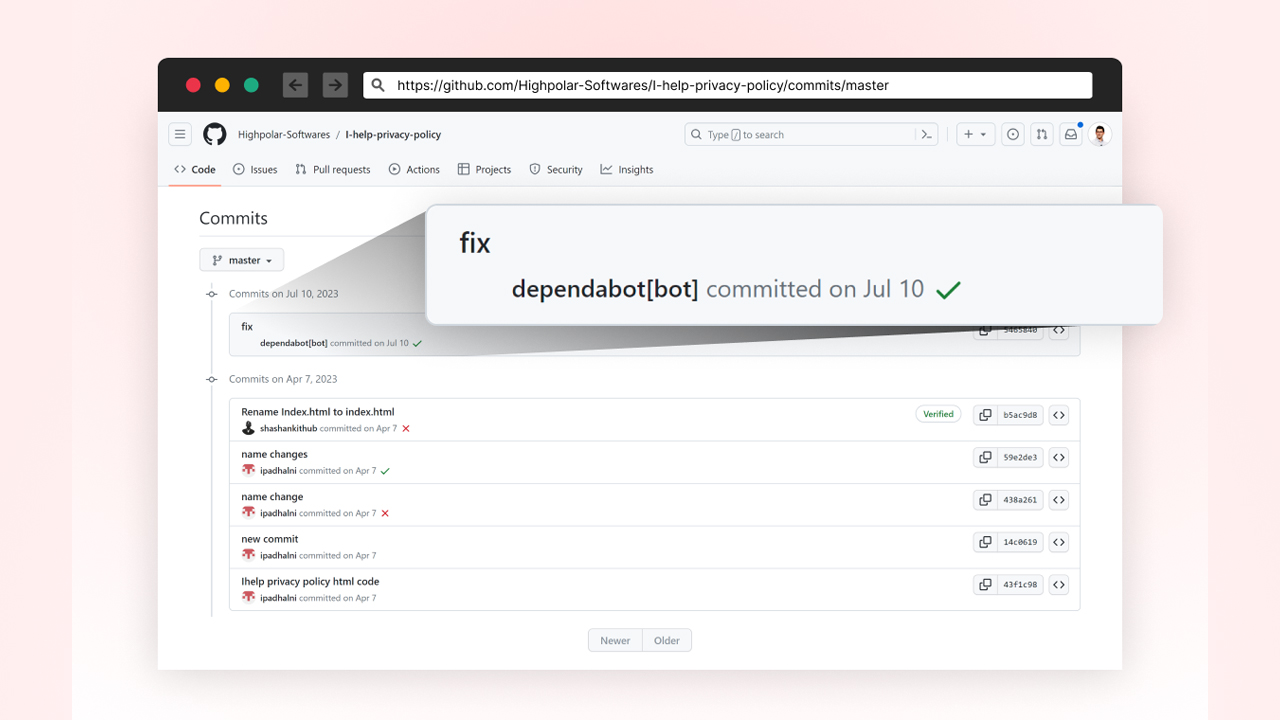
The latest attack, investigated by researchers at Checkmarx, showed threat actors mimicking Dependabot by changing the account alias to ‘dependabot[bot]’, along with a blank avatar.
Researchers said this was likely enough to convince most users that a commit had been legitimately made by Dependabot and that it didn’t warrant a second look.
Sign up today and you will receive a free copy of our Future Focus 2025 report - the leading guidance on AI, cybersecurity and other IT challenges as per 700+ senior executives
“This is the first incident [in which] we have witnessed a threat actor using fake git commits to disguise activity, knowing that many developers do not check the actual changes of Dependabot when they see it,” researchers said.
According to some of the affected users, GitHub personal access tokens (PATs) were stolen to gain access to projects. PATs offer an alternative method to authenticate access to GitHub without passwords and multi-factor authentication.
After stealing these, the threat actor was able to take over accounts that had access to projects, change their aliases to ‘dependabot[bot]’, and make malicious code commits.
Spoofing identities in attacks on GitHub projects
While the idea of forging commits in GitHub isn’t new, researchers said this is the first time they’ve seen Dependabot itself being spoofed in dependency-poisoning attacks.
It’s been known for well over a year that attackers are able to falsify commit dates to make an account appear more active than it actually has been, and spoof the identity of a contributor to poison GitHub projects, but the Dependabot tactic is a new one.
To mitigate any possibility of missing a malicious commit, GitHub introduced Commit Signature Verification which cryptographically signs commits to show they’ve been made by the genuine account holder rather than an attacker that has taken control of their account.
Checkmarx said there are limitations to the feature, in that unverified commits aren’t flagged to project contributors in an overt way. Commits receive a green ‘Verified’ tag next to them, which cannot be forged, but these rely on users being aware of what to look for and checking each one manually, and the user enabling ‘Vigilant Mode’ in their profile.
Researchers said they aren’t certain how the threat actor was able to acquire developers’ PATs, but they believe “the most likely scenario” is one that sees the developer’s computer infected with a malicious open source package that was able to steal the token and exfiltrate it via an attacker-controlled command and control (C2) server.
Once the threat actor was in control of the PATs, commits titled ‘fix’ were made to projects to install the password-stealing malware code.
Analysis showed this part of the attack was likely automated since in most cases researchers observed two common stages of code manipulation on the affected project.
The first saw a new workflow YAML file added to projects called ‘hook.yml’ which sends secrets and variables from the project to a URL - a process that’s re-triggered with every code push.
The second stage saw every single JavaScript file in a project manipulated. Every file with the ‘.js’ extension had an obfuscated line of code appended to the end of it so that once a web browser was launched, a separate script was downloaded from a URL and executed.
Anything inputted to web-based password forms from there on was intercepted and exfiltrated via the same attacker-controlled URL as the one used by the workflow file.
“This whole situation teaches us to be careful about where we get our code, even from trusted places like GitHub,” said Checkmarx. “It shows that even big platforms can have problems, so we need to always watch out and protect ourselves online.
RELATED RESOURCE

Discover how you can comply with multiple regulations and industry standards
DOWNLOAD FOR FREE
“To make things safer, consider switching to GitHub’s fine-grained personal access tokens. These tokens allow you to reduce the risk of compromised tokens. So, if someone bad gets one of these keys, they can't do a lot of damage.
“The attacker's tactics, techniques, and procedures (TTPs) involve the use of fake commits, stealing user credentials, and impersonating Dependabot to avoid detection, [and] show us supply chain attacks are getting more sophisticated as attackers realize it doesn’t take much to move silently.”

Connor Jones has been at the forefront of global cyber security news coverage for the past few years, breaking developments on major stories such as LockBit’s ransomware attack on Royal Mail International, and many others. He has also made sporadic appearances on the ITPro Podcast discussing topics from home desk setups all the way to hacking systems using prosthetic limbs. He has a master’s degree in Magazine Journalism from the University of Sheffield, and has previously written for the likes of Red Bull Esports and UNILAD tech during his career that started in 2015.
-
 Salesforce targets telco gains with new agentic AI tools
Salesforce targets telco gains with new agentic AI toolsNews Telecoms operators can draw on an array of pre-built agents to automate and streamline tasks
-
 Four national compute resources launched for cutting-edge science and research
Four national compute resources launched for cutting-edge science and researchNews The new national compute centers will receive a total of £76 million in funding
-
 Microsoft patches six zero-days targeting Windows, Word, and more – here’s what you need to know
Microsoft patches six zero-days targeting Windows, Word, and more – here’s what you need to knowNews Patch Tuesday update targets large number of vulnerabilities already being used by attackers
-
 An AWS CodeBuild vulnerability could’ve caused supply chain chaos – luckily a fix was applied before disaster struck
An AWS CodeBuild vulnerability could’ve caused supply chain chaos – luckily a fix was applied before disaster struckNews A single misconfiguration could have allowed attackers to inject malicious code to launch a platform-wide compromise
-
 Shai-Hulud malware is back with a vengeance and has hit more than 19,000 GitHub repositories so far — here's what developers need to know
Shai-Hulud malware is back with a vengeance and has hit more than 19,000 GitHub repositories so far — here's what developers need to knowNews The malware has compromised more than 700 widely-used npm packages, and is spreading fast
-
 GitHub is awash with leaked AI company secrets – API keys, tokens, and credentials were all found out in the open
GitHub is awash with leaked AI company secrets – API keys, tokens, and credentials were all found out in the openNews Wiz research suggests AI leaders need to clean up their act when it comes to secrets leaking
-
 Organizations urged to act fast after GitHub Action supply chain attack
Organizations urged to act fast after GitHub Action supply chain attackNews More than 20,000 organizations may be at risk following a supply chain attack affecting tj-actions/changed-files GitHub Action.
-
 Nearly a million devices were infected in a huge GitHub malvertising campaign
Nearly a million devices were infected in a huge GitHub malvertising campaignNews Microsoft has alerted users to a malvertising campaign leveraging GitHub to infect nearly 1 million devices around the world.
-
 'GitVenom' campaign uses dodgy GitHub repositories to spread malware
'GitVenom' campaign uses dodgy GitHub repositories to spread malwareNews Security researchers have issued an alert over a campaign using GitHub repositories to distribute malware, with users lured in by fake projects.
-
 Malicious GitHub repositories target users with malware
Malicious GitHub repositories target users with malwareNews Criminals are exploiting GitHub's reputation to install Lumma Stealer disguised as game hacks and cracked software