Ransomware is being rewritten in Go for joint attacks on Windows, Linux users
The Google-created programming language has become increasingly popular in the malware community for its speed and effectiveness in targeting more users with the same code base


Sign up today and you will receive a free copy of our Future Focus 2025 report - the leading guidance on AI, cybersecurity and other IT challenges as per 700+ senior executives
You are now subscribed
Your newsletter sign-up was successful
Cyber security researchers have discovered evidence of a years-old ransomware strain returning after being rewritten in Golang - a cross-platform programming language capable of reaching a higher number of users across different operating systems.
The TellYouThePass ransomware was first discovered in 2019, however researchers at Crowdstrike have now spotted a new strain being used as a second-stage attack following a successful exploit of the Log4Shell vulnerability revealed in December 2021.
The Java and .NET languages were used to create TellYouThePass before it emerged into circulation three years ago, but the pivot to Golang, often referred to as 'Go', has enabled attackers to target users across Windows and Linux with minimal changes to the malware's code.
Once encrypted, victims are greeted with a demand of 0.05 Bitcoin (£31,960) in return for a decryption tool to recover all their files.
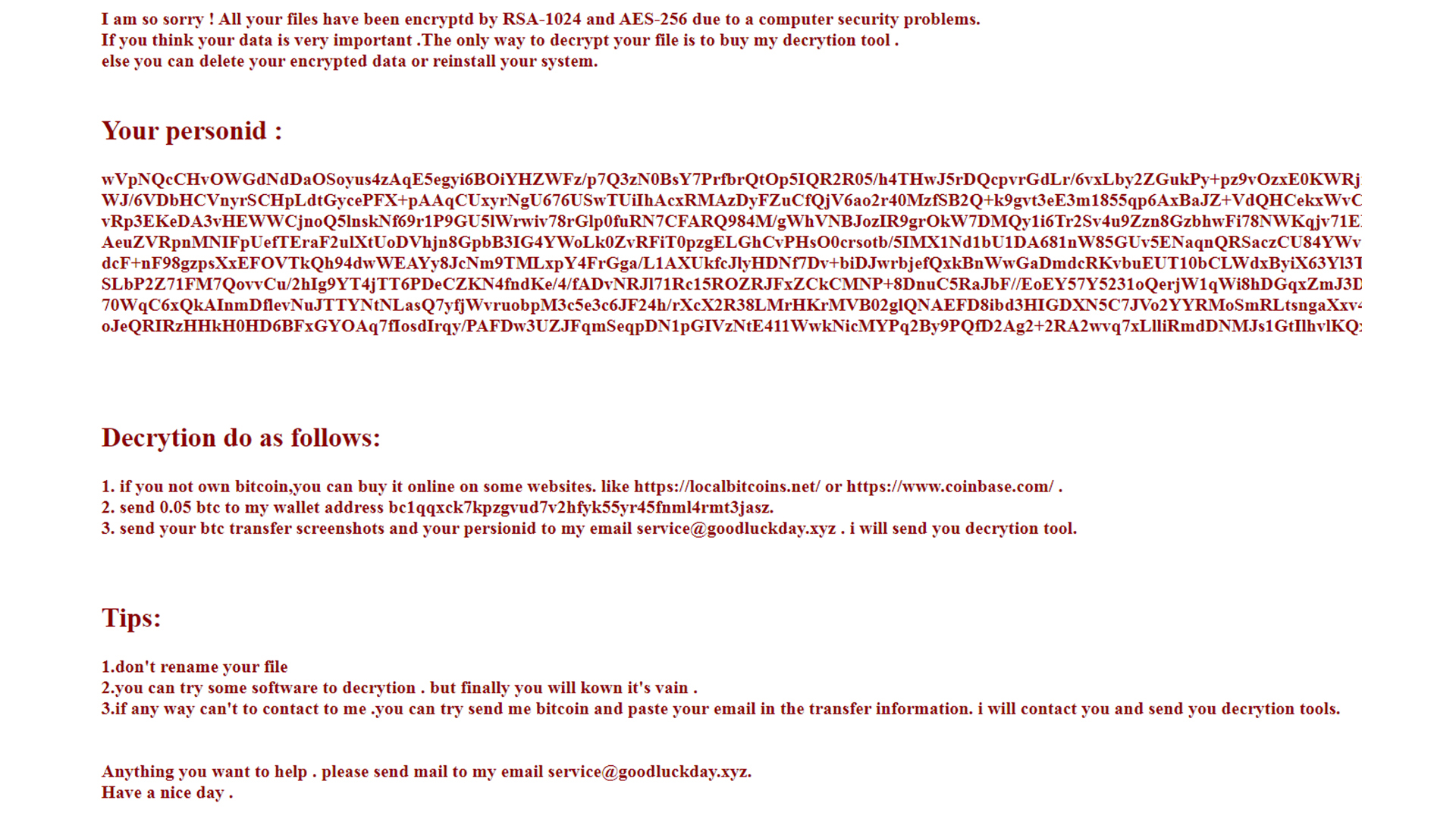
The ransom note displayed to victims
When examining code from malware targeting Windows and Linux machines, more than 85% of the code was near identical across the operating systems. This means Golang eliminates much of the leg work typically required to re-write malware for different operating systems, according to the researchers.
This interoperability has resulted in a steady growth in the popularity of Golang among malware authors over the past few years, according to Crowdstrike.
Sign up today and you will receive a free copy of our Future Focus 2025 report - the leading guidance on AI, cybersecurity and other IT challenges as per 700+ senior executives
Researchers noted that hackers who have re-written TellYouThePass in Golang have done so using a number of obfuscation techniques to make analysis of its code more difficult for researchers.
The binary of the malware is patched in the new version of TellYouThePass to make it difficult to use string-based signatures to detect that the malware is even written in Golang at all.
Hackers have also taken to randomising the names of the malware's functions, leaving just the main function easily identifiable - another tactic used to impede technical analysis of the ransomware.
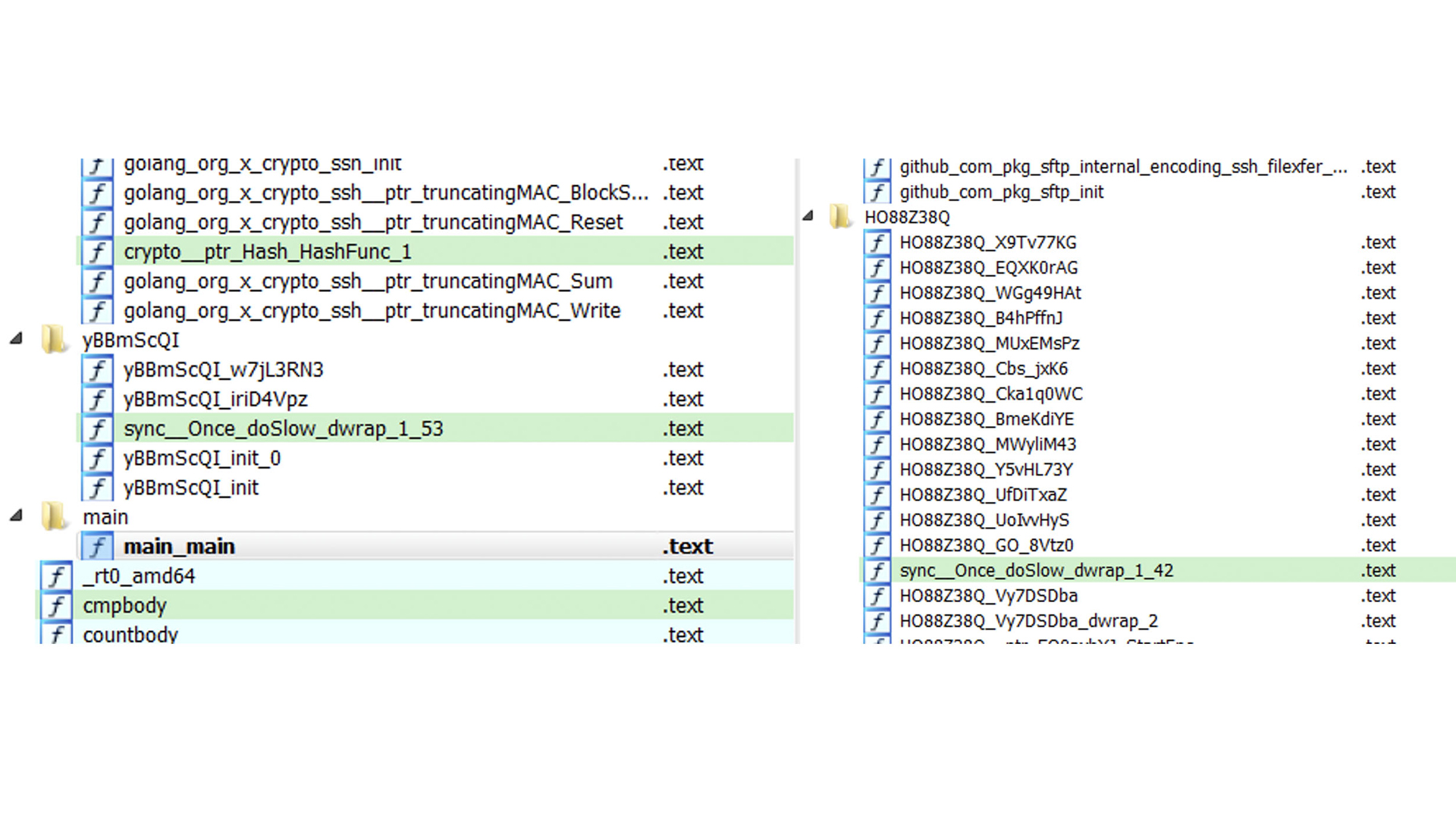
Analysis of TellYouThePass shows how function names are randomised
Before initiating the encryption routine, TellYouThePass attempts to kill certain tasks and processes, but on Linux this requires root privilege in order to perform that process. Such tasks include email clients, database applications, web servers, and document editors.
What is Golang?
Golang, or 'Go', is a versatile, cross-platform programming language created by Google in 2007 and is among the most in-demand languages currently in use by the IT community, according to the University of California, Berkeley.
Crowdstrike noted in a November 2021 report that it noticed a steep rise in uptake from the cyber crime community in 2021 with an 80% increase in use between June and August 2021.
The cyber security firm said cryptocurrency miners are the most popular form of malware using Golang with miners accounting for 70% of all Golang-written malware as of August 2021. As evidenced with TellYouThePass, ransomware is also seeing Golang uptake, as well as password-stealing trojans and downloaders, Crowdstrike said.
Among the other strains of ransomware written in Golang, the likes of Babuk and HelloKitty - the ransomware that targeted CD Projekt in 2021 - are the most prominent, according to cyber security firm Morphisec.
"Golang’s versatility has turned it into a one-stop shop for financially motivated eCrime developers," the company said in a blog post. "Instead of rewriting malware for Windows, macOS and Linux, eCriminals can use Golang to cross-compile the same codebase with ease, allowing them to target multiple platforms effortlessly."
RELATED RESOURCE

Despite having the ability to target users on a cross-platform basis, Crowdstrike said the vast majority (91%) of malware written in Golang targets Windows users - due to it market share, 8% is targeting users on macOS and just 1% of malware seeks to infect Linux machines.
Pivoting to Golang is also an attractive proposition given that it performs around 40 times faster than optimised Python code. Golang can run more functions than C++, for example, which makes for a more effective product that can be more difficult to analyse.
"Portability in malware means the expansion of the addressable market, in other words who might become a source of money," said Andy Norton, European cyber risk officer at Armis, speaking to IT Pro. "This isn’t the first time we've seen a shift towards more portable Malware; a few years ago we saw a change towards Java-based remote access trojans away from .exe Windows-centric payloads.
"The ability for security controls to inspect payloads is also another factor threat actors take into account, and drove the prevalence of file-less attacks up in recent years. The scrutiny and patching of Java currently on the back of Log4j vulnerabilities may be reducing Java's attractiveness as a threat vector and driving change in the criminal groups."

Connor Jones has been at the forefront of global cyber security news coverage for the past few years, breaking developments on major stories such as LockBit’s ransomware attack on Royal Mail International, and many others. He has also made sporadic appearances on the ITPro Podcast discussing topics from home desk setups all the way to hacking systems using prosthetic limbs. He has a master’s degree in Magazine Journalism from the University of Sheffield, and has previously written for the likes of Red Bull Esports and UNILAD tech during his career that started in 2015.
-
 Mistral CEO Arthur Mensch thinks 50% of SaaS solutions could be supplanted by AI
Mistral CEO Arthur Mensch thinks 50% of SaaS solutions could be supplanted by AINews Mensch’s comments come amidst rising concerns about the impact of AI on traditional software
-
 Westcon-Comstor and UiPath forge closer ties in EU growth drive
Westcon-Comstor and UiPath forge closer ties in EU growth driveNews The duo have announced a new pan-European distribution deal to drive services-led AI automation growth
-
 Ransomware gangs are using employee monitoring software as a springboard for cyber attacks
Ransomware gangs are using employee monitoring software as a springboard for cyber attacksNews Two attempted attacks aimed to exploit Net Monitor for Employees Professional and SimpleHelp
-
 Ransomware gangs are sharing virtual machines to wage cyber attacks on the cheap – but it could be their undoing
Ransomware gangs are sharing virtual machines to wage cyber attacks on the cheap – but it could be their undoingNews Thousands of attacker servers all had the same autogenerated Windows hostnames, according to Sophos
-
 Google issues warning over ShinyHunters-branded vishing campaigns
Google issues warning over ShinyHunters-branded vishing campaignsNews Related groups are stealing data through voice phishing and fake credential harvesting websites
-
 The FBI has seized the RAMP hacking forum, but will the takedown stick? History tells us otherwise
The FBI has seized the RAMP hacking forum, but will the takedown stick? History tells us otherwiseNews Billing itself as the “only place ransomware allowed", RAMP catered mainly for Russian-speaking cyber criminals
-
 Everything we know so far about the Nike data breach
Everything we know so far about the Nike data breachNews Hackers behind the WorldLeaks ransomware group claim to have accessed sensitive corporate data
-
 There’s a dangerous new ransomware variant on the block – and cyber experts warn it’s flying under the radar
There’s a dangerous new ransomware variant on the block – and cyber experts warn it’s flying under the radarNews The new DeadLock ransomware family is taking off in the wild, researchers warn
-
 Hacker offering US engineering firm data online after alleged breach
Hacker offering US engineering firm data online after alleged breachNews Data relating to Tampa Electric Company, Duke Energy Florida, and American Electric Power was allegedly stolen
-
 Cybersecurity experts face 20 years in prison following ransomware campaign
Cybersecurity experts face 20 years in prison following ransomware campaignTwo men used their tech expertise to carry out ALPHV BlackCat ransomware attacks