US indicts heart doctor for allegedly spearheading high-profile ransomware operations
The 55-year-old cardiologist profited from a ransomware side hustle and coached would-be hackers in using his tools for maximum rewards


A 55-year-old Venezuelan cardiologist has been charged in the US over allegedly being the mastermind behind the Jigsaw and Thanos ransomware operations.
Charges against Moises Luis Zagala Gonzalez were unsealed in federal court in Brooklyn, New York, on Monday and concern his alleged use and sale of ransomware, in addition to his support of and profit-sharing with other cyber criminals.
What is ransomware? The most popular ransomware strains targeting UK businesses How not to get hit by ransomware in 2022
Zagala resides in Ciudad Bolivar, Venezuela and also has citizenship in France. He is alleged to have created multiple high-profile ransomware tools in his spare time while primarily being a practising doctor.
A Federal Bureau of Investigation (FBI) source posed as a prospective cyber criminal and was able to discover how Zagala’s operation ran, how he generated multiple revenue streams, and how he ‘coached’ the cyber criminals into being more successful using the tools he created.
Zagala is alleged to have created the Jigsaw ransomware strain as well as the Thanos ‘ransomware builder’ - an application that allowed users to build their own ransomware program to be used alone or sold to the wider community.
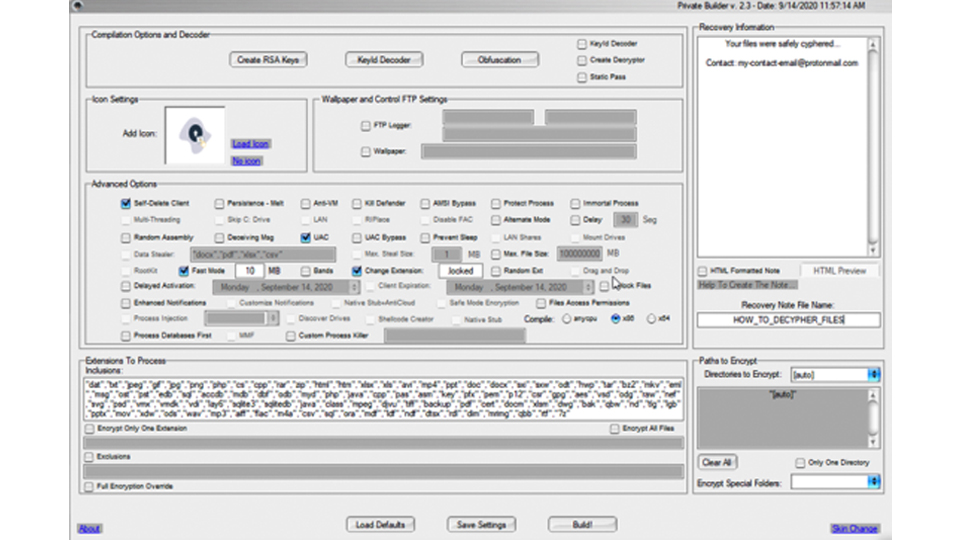
The Thanos application presented users with a GUI and an assortment of checkboxes to enable and disable certain features so effective ransomware programs could be built with little technical knowledge.
Such features included a data stealer that allowed users to select which types of files were stolen from a victim, an anti-VM feature that prevented researchers from loading it into a virtual machine for analysis and a self-delete function that destroyed the program after its use had become exhausted.
Sign up today and you will receive a free copy of our Future Focus 2025 report - the leading guidance on AI, cybersecurity and other IT challenges as per 700+ senior executives
Through the FBI’s source, the Bureau was able to understand how Thanos was sold through two licensing models.
Prospective users could either pay a single up-front fee for a limited license and have access to the program for a set time, or enrol into an affiliate program which saw the user receive a lifetime license in return for giving Zagala a portion of the profit generated from the ransomware it created.
The Depart of Justice (DoJ) said Zagala owned a server in Charlotte, North Carolina that checked if a user’s license was valid or not.
After the FBI source request to join Zagala’s affiliate program was refused as there weren’t enough open places at the time, but Zagala offered to license Thanos for $500 per month with basic options, or $800 per month with full functionality.
There were only a maximum of 10-20 spots available on Zagala’s affiliate program at any one time, and sometimes as few as five, he said, according to the DoJ’s official complaint.
Thanos was advertised on “various” cyber crime forums and the listings were accompanied by Zagala’s claims that the ransomware software Thanos generated was nearly undetectable by anti-virus programs and due to the encryption and self-deletion functionality, recovery was almost impossible for victims.
Conversations between Zagala and the FBI source revealed that he would instruct buyers on how to craft ransom notes, steal passwords, and set Bitcoin addresses to receive payment.
Zagala would take time to explain exactly how the software works and encourage happy customers to leave positive reviews of which there were many, with some claiming to have made good profit after infecting thousands of computers.
RELATED RESOURCE

The Total Economic Impact™ of Mimecast
Cost savings and business benefits enabled by using Mimecast with Microsoft 365
FREE DOWNLOAD
Zagala even spent time explaining to the source how to set up a successful ransomware organisation and establish an affiliate program of their own before offering an additional free two-week license after the source’s one-month trial ended, telling the source “because one month is too little for this business… sometimes you need to work a lot to get good profit”.
“As alleged, the multi-tasking doctor treated patients, created and named his cyber tool after death, profited from a global ransomware ecosystem in which he sold the tools for conducting ransomware attacks, trained the attackers about how to extort victims, and then boasted about successful attacks, including by malicious actors associated with the government of Iran,” said Breon Peace, United States Attorney for the Eastern District of New York.
“Combating ransomware is a top priority of the Department of Justice and of this Office,” he added. “If you profit from ransomware, we will find you and disrupt your malicious operations.”
If convicted, Zagala will face a maximum of ten years in US prison - five years for attempted computer intrusion, and a further five for conspiracy to commit computer intrusions.

Connor Jones has been at the forefront of global cyber security news coverage for the past few years, breaking developments on major stories such as LockBit’s ransomware attack on Royal Mail International, and many others. He has also made sporadic appearances on the ITPro Podcast discussing topics from home desk setups all the way to hacking systems using prosthetic limbs. He has a master’s degree in Magazine Journalism from the University of Sheffield, and has previously written for the likes of Red Bull Esports and UNILAD tech during his career that started in 2015.
-
 Everything we know so far about the Nike data breach
Everything we know so far about the Nike data breachNews Hackers behind the WorldLeaks ransomware group claim to have accessed sensitive corporate data
-
 There’s a dangerous new ransomware variant on the block – and cyber experts warn it’s flying under the radar
There’s a dangerous new ransomware variant on the block – and cyber experts warn it’s flying under the radarNews The new DeadLock ransomware family is taking off in the wild, researchers warn
-
 Hacker offering US engineering firm data online after alleged breach
Hacker offering US engineering firm data online after alleged breachNews Data relating to Tampa Electric Company, Duke Energy Florida, and American Electric Power was allegedly stolen
-
 Cybersecurity experts face 20 years in prison following ransomware campaign
Cybersecurity experts face 20 years in prison following ransomware campaignTwo men used their tech expertise to carry out ALPHV BlackCat ransomware attacks
-
 15-year-old revealed as key player in Scattered LAPSUS$ Hunters
15-year-old revealed as key player in Scattered LAPSUS$ HuntersNews 'Rey' says he's trying to leave Scattered LAPSUS$ Hunters and is prepared to cooperate with law enforcement
-
 The Scattered Lapsus$ Hunters group is targeting Zendesk customers – here’s what you need to know
The Scattered Lapsus$ Hunters group is targeting Zendesk customers – here’s what you need to knowNews The group appears to be infecting support and help-desk personnel with remote access trojans and other forms of malware
-
 Impact of Asahi cyber attack laid bare as company confirms 1.5 million customers exposed
Impact of Asahi cyber attack laid bare as company confirms 1.5 million customers exposedNews No ransom has been paid, said president and group CEO Atsushi Katsuki, and the company is restoring its systems
-
 The US, UK, and Australia just imposed sanctions on a Russian cyber crime group – 'we are exposing their dark networks and going after those responsible'
The US, UK, and Australia just imposed sanctions on a Russian cyber crime group – 'we are exposing their dark networks and going after those responsible'News Media Land offers 'bulletproof' hosting services used for ransomware and DDoS attacks around the world

