Kali Linux review: A swiss army knife for cyber security pros
Use Kali Linux for good, not evil – and forge a career in cybersecurity while you're at it

-
+
Host of tools
-
+
Suitable for all levels
-
+
Value for money
- +

With the current shortage of skills, there are plenty of career opportunities for people interested in cybersecurity. Luckily, there are plenty of tools too. One of the most respected is Kali, a secure Debian Linux-based distribution specifically targeting penetration testers and digital forensics experts. The company that makes it, Offensive Security (Offsec), unveiled it in 2013. It recently released the tenth-anniversary edition of the distro, 2023.1, so we thought it was time we took a look.
You don't need to use Kali for penetration testing. It's essentially Debian with a collection of third-party tools, all of which you can install yourself from elsewhere. However, this distro offers some distinct advantages.
The first is convenience. Offsec has bought hundreds of tools together in this OS, organizing them neatly in a thoughtfully designed menu system.
Another advantage is Kali's focus on its own security. It uses a minimal, trusted set of repositories to host additional programs. It also has a customized version of the kernel, fitted with a patch to support wireless injection for pen testing, along with support for many external wireless cards. The default installation also comes with network services disabled so that you don't accidentally announce yourself to your target network when you turn it on.
Kali is also a rolling release distribution, meaning that its developers work with a single code branch, delivering frequent regular releases with updated versions of the software. This contrasts with many other distributions, which work on less frequently released discrete versions in different code branches. At the time of writing, Offsec had already dropped 2023.2, just ten weeks after 2023.1.
Kali Linux review: Installation
Kali has a comprehensive set of installation options. It offers pre-based VMware and VirtualBox virtual machine images with configuration taken care of. Offsec has already released version 2023.2, adding a pre-baked VM image for Microsoft's Hyper-V.
We installed the VirtualBox VM for testing purposes, but this popular specialist distro is becoming increasingly appropriate as a bare-metal installation for IT pros. Offsec removed root privileges from the default Kali account in the 2020.1 release as it became the primary OS for more users.
Sign up today and you will receive a free copy of our Future Focus 2025 report - the leading guidance on AI, cybersecurity and other IT challenges as per 700+ senior executives
If you're running in a virtual machine, you might want to set the network adapter in your VirtualBox settings to connect in bridge mode rather than NAT mode, so that you can conduct ARP-based sessions on your local network. The same goes for Metasploitable. This is the target OS that we'll use for testing out Kali Linux's hacking capabilities.
Kali Linux review: Design
Kali looks great out of the box, with a series of 2023 wallpapers. Here's the default:

However, you can change the desktop environment to suit your needs. The VirtualBox image comes with XFCE by default, but you can also use KDE, Gnome, or Mate, among others. If you want to get more esoteric, Kali's repositories offer a pre-cooked version of i3, which dispenses with the traditional desktop metaphor altogether, focusing instead on tiled windows and keyboard-intensive operation.
Kali also comes with a fun tool out of the box: a stealth mode for hackers in the field. If you're on-site with a client trying to gain access, you can type kali-undercover into the terminal. Voila! Kali's interface switches to look like a Windows box to avoid drawing attention. Just re-enter the command to switch back.
Kali Linux review: Tools
007-style UI gadgets aside, the tools are what's really important in Kali. They're why we're here – and this OS has oodles of them. They cover the standard stages of a penetration test – reconnaissance, scanning, exploitation, maintaining access, and reporting. Some menu categories like information gathering and reporting map directly to these, but you'll need to find other tools in different menu categories, like Web Application Analysis, Wireless Attacks, Database Assessment, and Forensics. Some tools, like the Swiss Army knife of target enumeration, Maltego, appear in multiple categories.
You won't find all of the available tools out of the box unless you download the behemoth 10Gb 'everything' installer in Kali's download section, but this isn't available as a VirtualBox image. No matter, though; Kali offers metapackages in its repositories that allow us to install different groups of add-in components for the OS. These are grouped into categories like the aforementioned desktop environments, along with tool categories like Bluetooth hacking programs.
We can install the lot with sudo apt install kali-linux-everything. Only do this if you've a fast connection and time to spare. Now go make a cuppa and watch Kali install some fun tools like the Active Directory enumeration package Bloodhound, and the NSA's open-sourced Ghidra reverse engineering package.
Even after installing this mega-collection you might miss one or two tools that are in the latest editions of the OS and don't seem to have made it into the 'everything' metapackage. For example, the 2023.1 release bought us access to several new goodies, including the Arkime package capture program, and a set of browser-based data manipulation tools called CyberChef. It also introduced DefectDojo, an open-source platform that helps security pros to track vulnerabilities and assign tasks to fix them via third-party collaboration tools. Another package is Redeye, a tool from the US Department of Homeland Security for managing pen test data.
2023.2 which bought even more toys. Notable among them were Evilginx2 (a framework to run manipulator in the middle attacks), the GoPhish open-source phishing toolkit, and TheHive, a security incident response platform. You might have to install some of these manually depending on your installation choices, but it only takes a single command.
The menu system subdivides into even more categories. For example, Information Gathering subdivides into menus like OSINT (open-source intelligence) analysis, DNS analysis, and route analysis.
Kali Linux review: The network
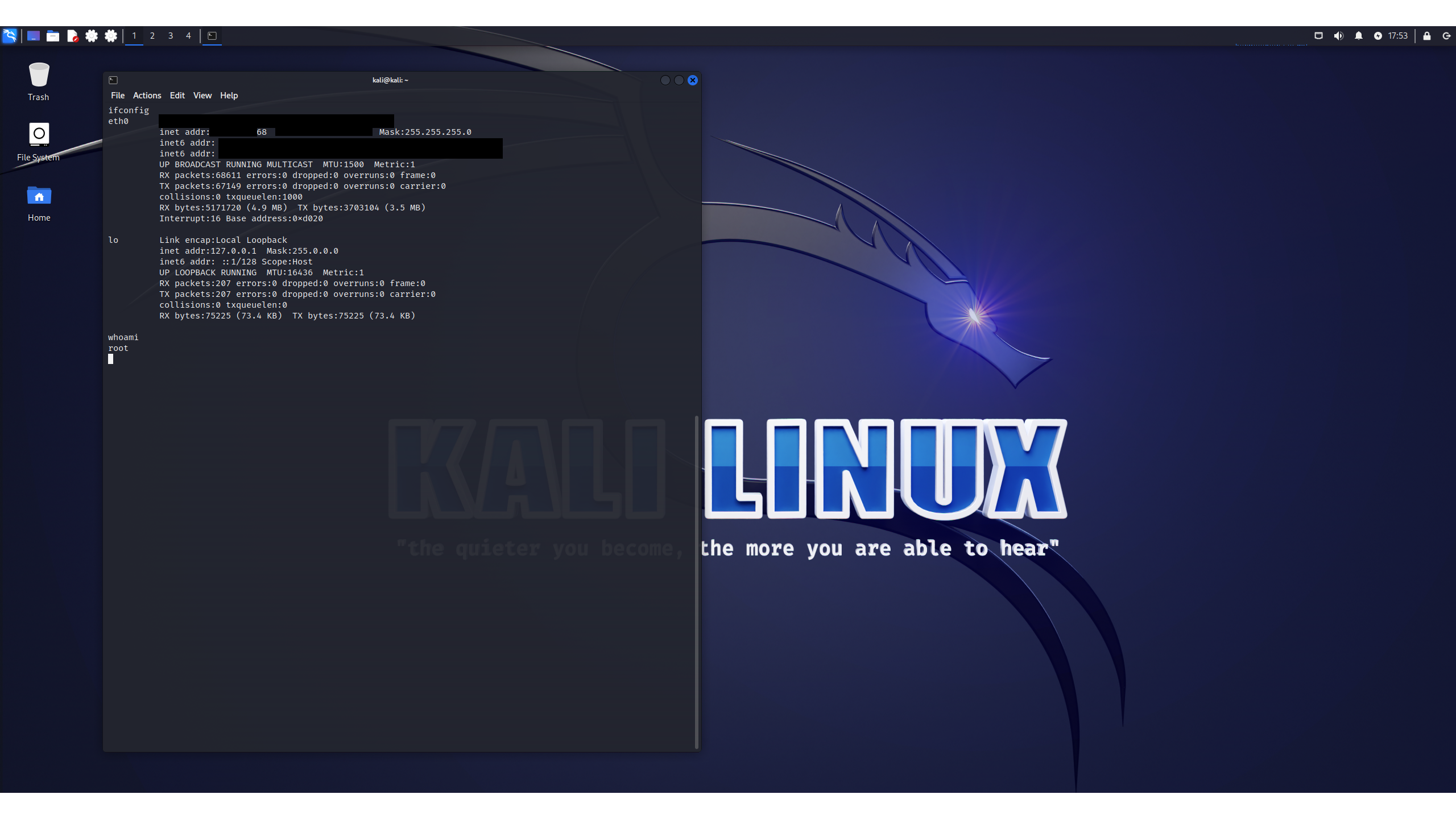
We're looking for Metasploitable, the training VM for pen testers that we're running on our network. We could identify it by switching to it and typing ifconfig, but let's do it from Kali.
The Information Gathering menu is where you'll find some of the enumeration tools that you'll use early on in your pen test projects. For example, Netdiscover enables you to quickly and quietly find out what's on your local network. A lot of tools, such as this one, have no GUI but instead throw you straight into a terminal displaying their help file.
We can use Netdiscover for a quick enumeration of our network:

Note that this command still requires sudo access, but Offsec has been loosening restrictions for key services. The tenth anniversary edition no longer required root access to the kernel logs via dmseg, for example, and it also gives you access to privileged ports (those below 1024) without root. That's useful, given that some tools you'll run in non-root modes, like Metasploit, often need access to those ports.
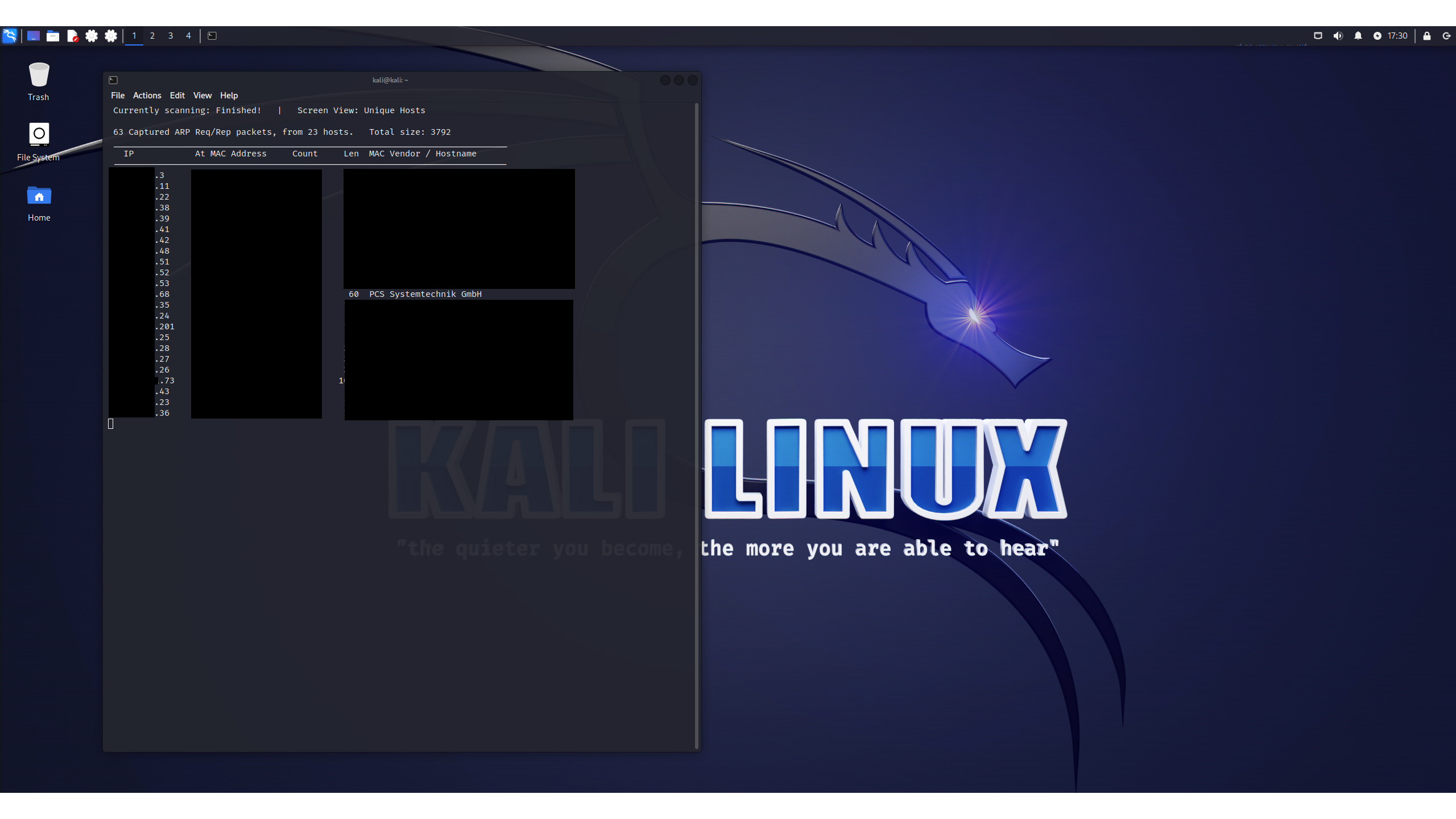
We've redacted the IPs and devices on the test network (even though they're internal), leaving just one result: a system supposedly from PCS Systemtechnik GmBH.
There's a strange story here. The OUI - the first three octets of a device's MAC address – identifies the organization that registered that address. Netdiscover uses this to find out who made the device. Innotek, the company that originally produced VirtualBox before Sun Microsystems acquired it in 2008, never got around to registering a MAC address for the product. Instead, Sun was going to do it, but apparently didn't.
For years the OUI belonged to a company called Cadmus Systems until 2016, when it switched to PCS. Neither of these companies have anything to do with VirtualBox, which is now an open-source project maintained by Oracle. However, this OUI – 08:00:27 – is the default for VirtualBox, so assuming that an admin doesn't change it, looking for PCS is a handy way to quickly spot likely candidates for VirtualBox VMs on the network.
Other than the Kali VM we're operating, this is the only VirtualBox VM operating in our lab, so it must be Metasploitable. Let's drill down on that IP address and see which services are running on that target VM. We'll use Nmap for this with the -sV modifier, which tells it to list the services and their version numbers running on each port. It delivers a handy list:
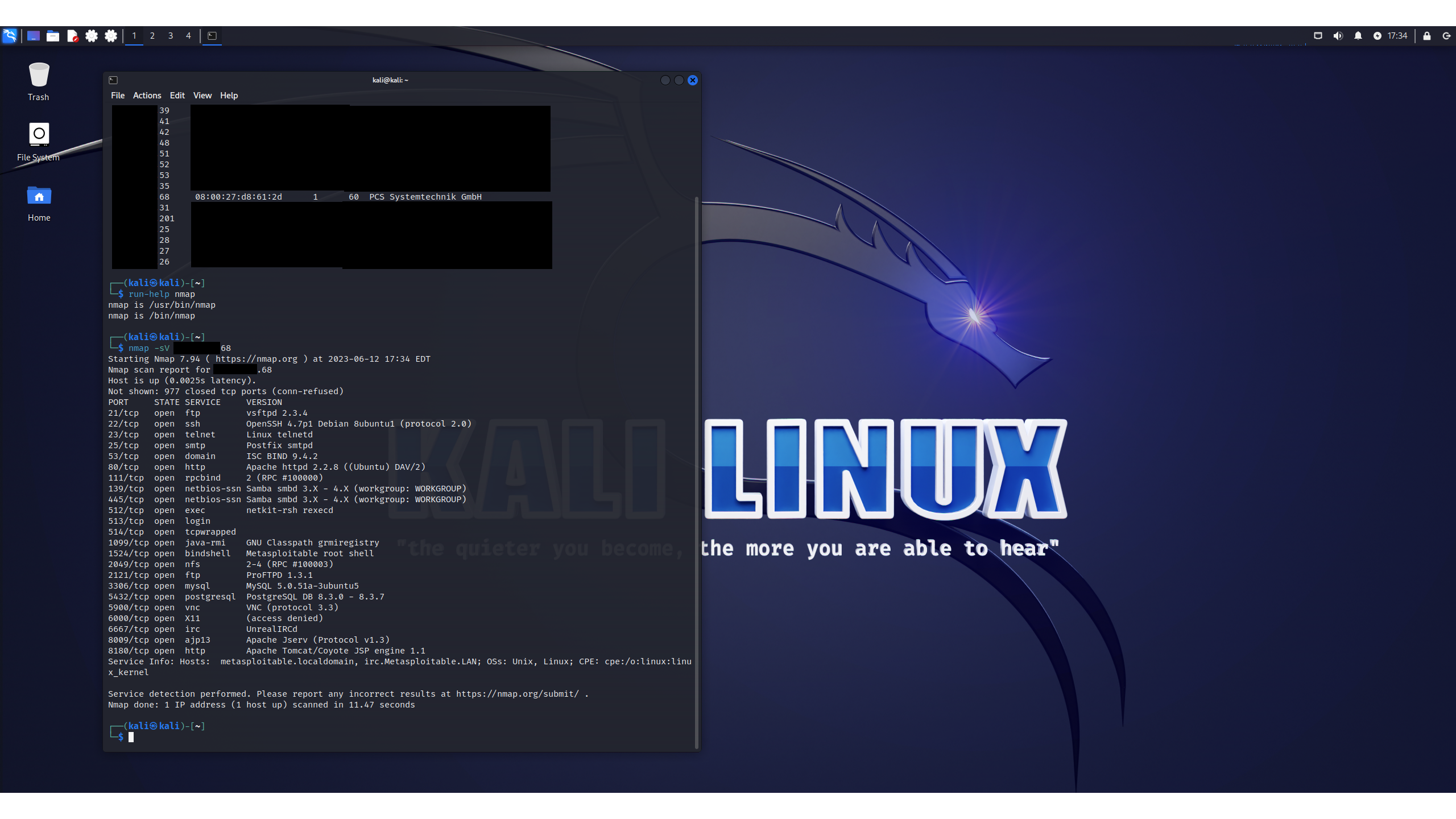
Good admins shut down services that aren't needed, but Metasploitable is designed for training pen testers, meaning that it's intentionally configured with more holes than a slice of Gruyere. Let's try the first service we find. Nmap tells us what software is running on this open FTP port, along with the version number.
Kali Linux review: Metasploit FTW
At this point, we can break out one of the most useful tools in Kali: Metasploit, the open-source tool originally developed by H.D. Moore 20 years ago and now owned by Rapid7 (which also publishes Metasploitable). It is a framework containing hundreds of known exploits, enabling you to launch them against controlled targets. We'll start it using msfconsole and then search for the server's FTP tool, vsftp:
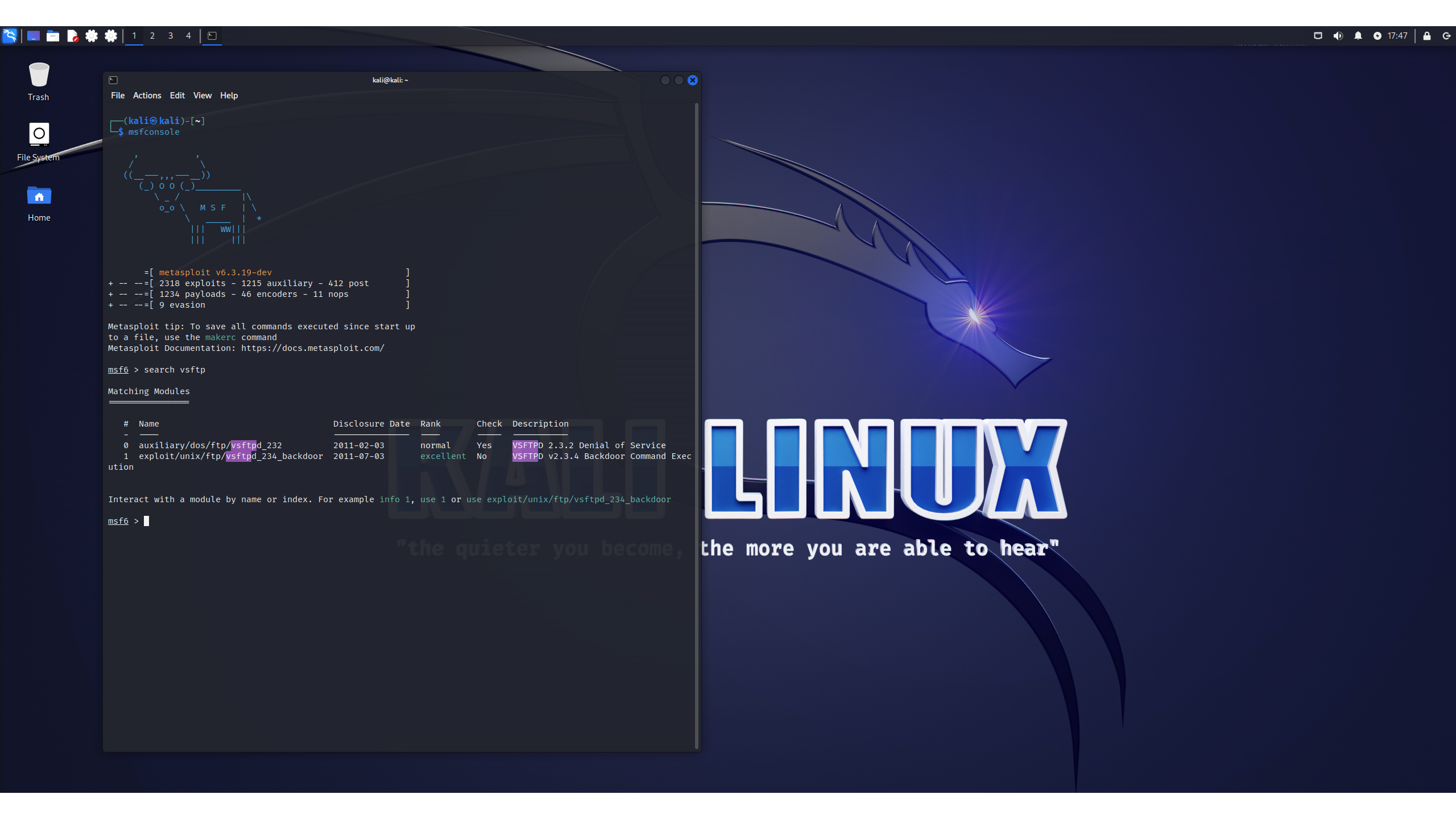
We get two exploits in our results. Both were disclosed long before Kali was even released, and should have been patched by any competent admin. Note that these are compatible with the version number of the software that this vulnerable server is using.
We can use Metasploit to attack this software. We won't show the specific steps involved because we don't want to teach bad-faith actors how to hack boxes that they don't own, but here's the shell that Metasploit gave us when it was done. Note that the IP address in the shell is the target system's, and we have root status.
This fun piece of script-kiddery shows how quickly Kali can yield results, but it barely scratches the surface of what's available. This friendly, functional system offers so many possibilities that would take months, if not years, to fully understand all of the tools on offer.
Kali Linux review: Purchasing
Kali isn't just one product; it's a whole family. There's Kali Purple, a collaborative system for red and blue teams to work together on system hardening, and Kali NetHunter, a version of Kali for Android phones. It's a great free resource for those interested in a career defending networks.
Don't let Kali's smooth operation and attractive desktop fool you: it isn't intended for beginners. It's a pared-down system with security in mind, meaning that you won't find as much software as you might in the sprawling Ubuntu or Arch repositories.
If you're new to Linux or just want an alternative to Windows, start with another distro. You can still install all of the Kali tools on alternative systems as you need them, and then switch to Kali when you've developed some basic Linux chops.
Oh, and the mandatory warning applies: Kali is intended for training, and for testing systems to which you have authorized access. It is not for breaking into other people's stuff. Attempting to use it in this way is dangerous to the target, and will also likely land you in jail. Use this hacking powerhouse for good, not evil – and forge yourself a career in cyber security while you're at it.
Danny Bradbury has been a print journalist specialising in technology since 1989 and a freelance writer since 1994. He has written for national publications on both sides of the Atlantic and has won awards for his investigative cybersecurity journalism work and his arts and culture writing.
Danny writes about many different technology issues for audiences ranging from consumers through to software developers and CIOs. He also ghostwrites articles for many C-suite business executives in the technology sector and has worked as a presenter for multiple webinars and podcasts.
-
 CISA’s interim chief uploaded sensitive documents to a public version of ChatGPT – security experts explain why you should never do that
CISA’s interim chief uploaded sensitive documents to a public version of ChatGPT – security experts explain why you should never do thatNews The incident at CISA raises yet more concerns about the rise of ‘shadow AI’ and data protection risks
By Ross Kelly Published
-
 Former Google engineer convicted of economic espionage after stealing thousands of secret AI, supercomputing documents
Former Google engineer convicted of economic espionage after stealing thousands of secret AI, supercomputing documentsNews Linwei Ding told Chinese investors he could build a world-class supercomputer
By Emma Woollacott Published
-
 OpenAI admits 'losing access to GPT‑4o will feel frustrating' for users – the company is pushing ahead with retirement plans anway
OpenAI admits 'losing access to GPT‑4o will feel frustrating' for users – the company is pushing ahead with retirement plans anwayNews OpenAI has confirmed plans to retire its popular GPT-4o model in February, citing increased uptake of its newer GPT-5 model range.
By Ross Kelly Published
