Duo unravels massive three-tiered ‘crypto-giveaway’ botnet
Researchers used a machine learning model to weed through 88 million Twitter accounts for bots and spammers


Researchers have uncovered a sophisticated botnet perpetuating a cryptocurrency scam in one of the most wide-reaching studies of the Twitter ecosystem to date.
Comprised of at least 15,000 bots in a three-tiered hierarchical structure, a team of Duo Security researchers observed how the crypto-scam botnet worked to spread a fake 'cryptocurrency giveaway', and evolved over time to remain undetected.
Duo's principal R&D engineer Jordan Wright and data scientist Olabode Anise published their findings in a report titled 'Dont @ Me: Hunting Twitter Bots at Scale', ahead of a presentation at the 2018 Black Hat cybersecurity conference in Las Vegas tomorrow.
As part of the process, the researchers analysed more than 88 million Twitter accounts - one of the largest random Twitter datasets to date - between May and July 2018, and processed their APIs in a machine learning model to differentiate a human account from a bot.
The crypto-giveaway botnet, according to Duo, would first involve bots spoofing a legitimate cryptocurrency-associated account by stealing its display name and avatar. These accounts would subsequently spread fake links in replies to genuine users' tweets, and were also seen to take on the identity of a celebrity, or news organisation.
The team then learned many of them followed the same Twitter accounts, declared "hub accounts". They were unclear as to the exact contribution these accounts made to the botnet, but theorised they are "randomly chosen accounts which the bots follow in an effort to appear legitimate".
Amplification bots, fake accounts that exist purely to like tweets to artificially inflate their popularity and visibility, comprised the final tier of this structure and were deployed to raise the prominence of the tweets promoting the scam, as well as afford them legitimacy.
Sign up today and you will receive a free copy of our Future Focus 2025 report - the leading guidance on AI, cybersecurity and other IT challenges as per 700+ senior executives
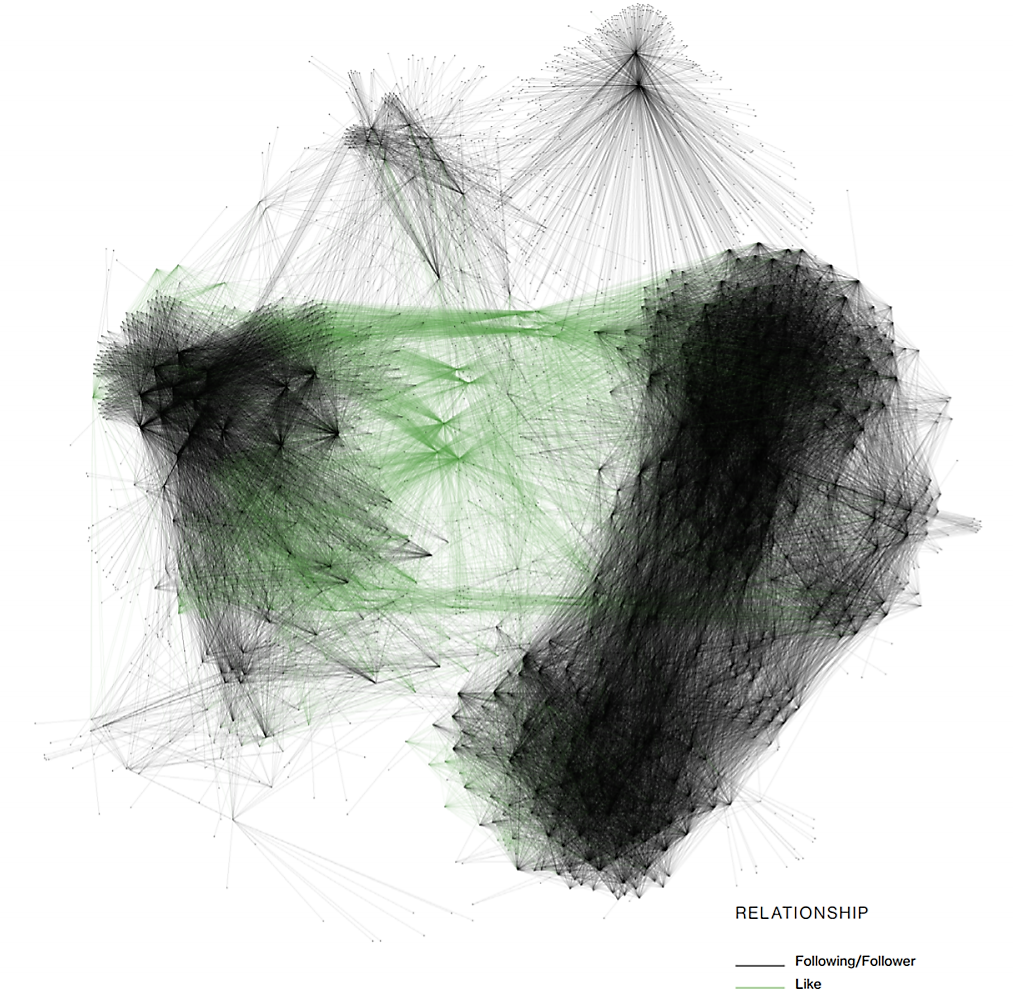
They mapped the relationship between the amplification bots, and the bots they support, to discover previously unknown accounts; in turn performing further analysis to unravel a sophisticated structure. In this process they established it was possible to follow a thread "that can result in the unraveling of the entire botnet".
"Users are likely to trust a tweet more or less depending on how many times it's been retweeted or liked. Those behind this particular botnet know this, and have designed it to exploit this very tendency," Duo's Anise said.
"Malicious bot detection and prevention is a cat-and-mouse game," Wright added. "We anticipate that enlisting the help of the research community will enable discovery of new and improving techniques for tracking bots. However, this is a more complex problem than many realize, and as our paper shows, there is still work to be done."
The tools and techniques the pair used to uncover the cryptocurrency scam botnet, which they are set to highlight at Black Hat, are being made publicly available via Github following their presentation.
Although botnets can be structured in different ways, the paper noted the structure and appearance of this particular one resembled the 'diet-spam botnet' discovered by Symantec in 2015 - with dedicated roles assigned to different clusters. Alternatively, botnets may exist in a 'flat' structure where each fake account exhibits the same behaviour.
"Twitter is aware of this form of manipulation and is proactively implementing a number of detections to prevent these types of accounts from engaging with others in a deceptive manner," a company spokesperson said.
"Spam and certain forms of automation are against Twitter's rules. In many cases, spammy content is hidden on Twitter on the basis of automated detections.
"When spammy content is hidden on Twitter from areas like search and conversations, that may not affect its availability via the API. This means certain types of spam may be visible via Twitter's API even if it is not visible on Twitter itself. Less than 5% of Twitter accounts are spam-related."
Writing in a blogpost, the principal researchers said they were pleased with Twitter's initial response to their findings, and the company's announcement that it would be challenging "more than 9.9 million potentially spammy or automated accounts per week".
"We're excited to see these efforts by Twitter and are hopeful that these increased investments will be effective in combating spam and malicious content," the pair wrote.
"However, we don't consider the problem solved. The case study presented in this paper demonstrates that organized botnets are still active and can be discovered with relatively straightforward analysis."

Keumars Afifi-Sabet is a writer and editor that specialises in public sector, cyber security, and cloud computing. He first joined ITPro as a staff writer in April 2018 and eventually became its Features Editor. Although a regular contributor to other tech sites in the past, these days you will find Keumars on LiveScience, where he runs its Technology section.
-
 Hackers are using LLMs to generate malicious JavaScript in real time
Hackers are using LLMs to generate malicious JavaScript in real timeNews Defenders advised to use runtime behavioral analysis to detect and block malicious activity at the point of execution, directly within the browser
-
 Developers in India are "catching up fast" on AI-generated coding
Developers in India are "catching up fast" on AI-generated codingNews Developers in the United States are leading the world in AI coding practices, at least for now
-
 Russian hackers are using an old Cisco flaw to target network devices – here’s how you can stay safe
Russian hackers are using an old Cisco flaw to target network devices – here’s how you can stay safeNews With the aim of carrying out espionage, Russia's Center 16 is targeting infrastructure organizations around the world
-
 HPE eyes enterprise data sovereignty gains with Aruba Networking Central expansion
HPE eyes enterprise data sovereignty gains with Aruba Networking Central expansionNews HPE has announced a sweeping expansion of its Aruba Networking Central platform, offering users a raft of new features focused on driving security and data sovereignty.
-
 Fortify your future: How HPE ProLiant Servers deliver top-tier cyber security, management, and performance
Fortify your future: How HPE ProLiant Servers deliver top-tier cyber security, management, and performanceWhitepaper Deploy servers with a secure approach
-
 Fortify your future with HPE ProLiant Servers powered by Intel
Fortify your future with HPE ProLiant Servers powered by IntelWhitepaper Enhance your security and manage your servers more effectively
-
 Architecting enterprise networks for the next decade
Architecting enterprise networks for the next decadeWhitepaper A new paradigm in network architecture
-
 Why network monitoring tools fail within secure environments
Why network monitoring tools fail within secure environmentsWhitepaper Gain visibility into devices, networks, and applications
-
 Better together: HPE Aruba Networking CX switches and HPE Aruba Networking Central
Better together: HPE Aruba Networking CX switches and HPE Aruba Networking CentralWhitepaper Explore the power and simplicity of managing HPE Aruba Networking CX Switches with HPE Aruba Networking Central
-
 Cyber-resilient infrastructure starts with server security
Cyber-resilient infrastructure starts with server securitywhitepaper Take a security-focused approach when investing in the next wave of IT infrastructure.