Windows XP source code allegedly leaked online
The suspected Microsoft operating system files were spread on the anonymous forum 4chan

Sign up today and you will receive a free copy of our Future Focus 2025 report - the leading guidance on AI, cybersecurity and other IT challenges as per 700+ senior executives
You are now subscribed
Your newsletter sign-up was successful
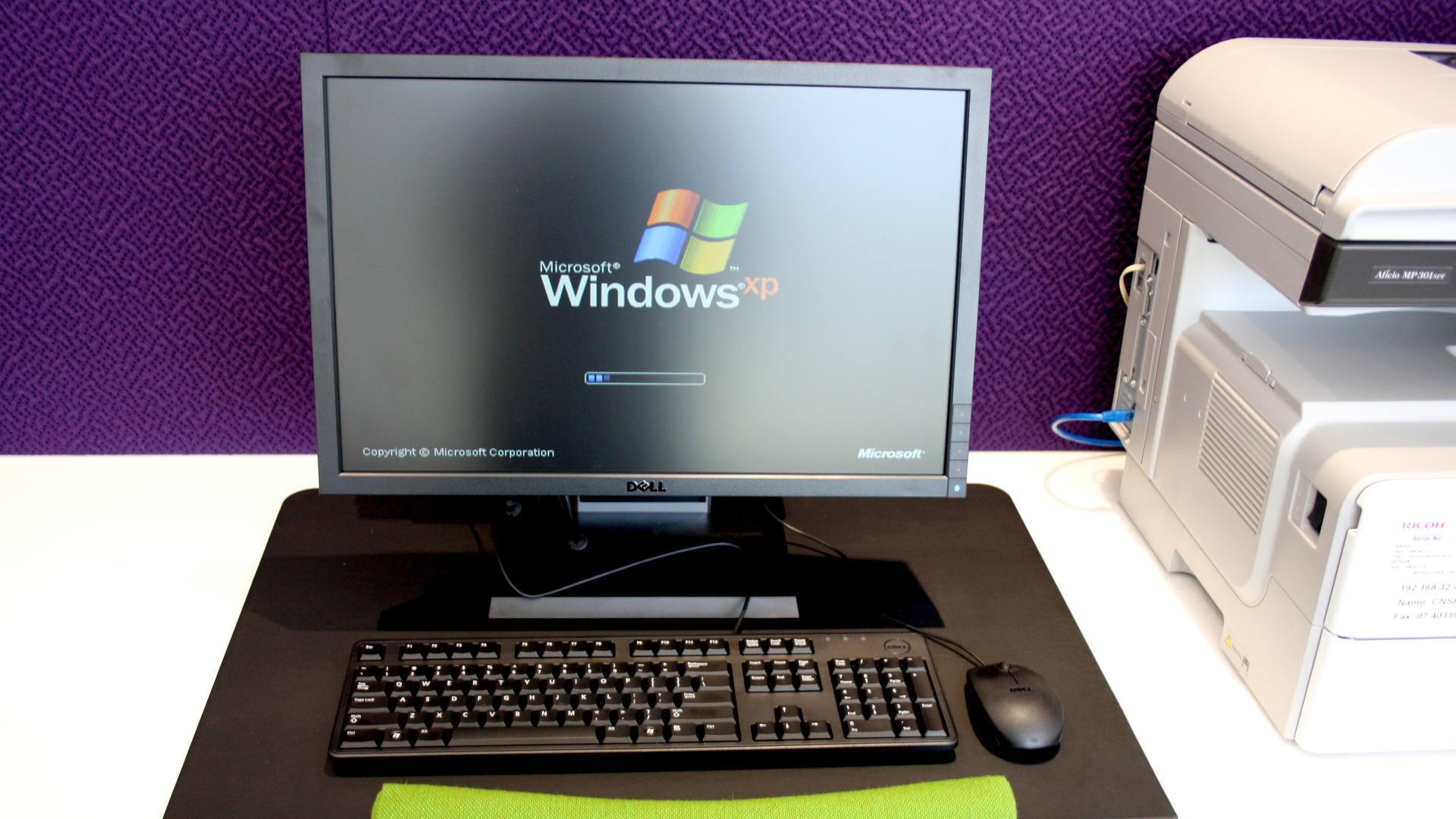
The source code for various versions of Microsoft Windows operating systems have been allegedly leaked online, following the discovery of files on an online forum.
The files, spread on the anonymous forum 4chan, contained the alleged source codes for Windows XP SP1, Windows NT 3.5, as well as the original Xbox.
Although the legitimacy of the files have been questioned by 4chan users, some security researchers believe that the source codes could be genuine.
Cylance principal software architect Greg Linares said on Twitter that the leaked source code for the Windows XP SP1 operating system, originally released in 2002, “looks pretty legit”.
The screenshot of the files was posted by Twitter user @RoninDey, who claimed that the source codes were “bundled in the torrent” and uploaded onto cloud storage and file hosting service Mega.
The Windows XP operating system has not been supported by Microsoft since 2014. Likewise, Windows NT 3.5 stopped being supported in 2001.
However, some has raised concerns that the leak could allow hackers to spot code that was potentially reused in later versions of Windows.
Sign up today and you will receive a free copy of our Future Focus 2025 report - the leading guidance on AI, cybersecurity and other IT challenges as per 700+ senior executives
"It is important to remember that Operating Systems are constantly evolving, meaning that the old source code could provide clues that allow hackers to spot vulnerabilities in the more recent versions," said Ray Walsh, digital privacy expert at ProPrivacy.
RELATED RESOURCE

Managing security risk and compliance in a challenging landscape
How key technology partners grow with your organisation
"Although Microsoft completely stopped providing updates and support for the deprecated XP operating system in 2014, there is ample evidence that the NHS and UK ambulances still operate systems using the defunct operating system.
"This means that the recent leak of the Windows XP source code could be much more problematic than first meets the eye."
A Microsoft spokesperson told IT Pro that the company is "investigating the matter".
Having only graduated from City University in 2019, Sabina has already demonstrated her abilities as a keen writer and effective journalist. Currently a content writer for Drapers, Sabina spent a number of years writing for ITPro, specialising in networking and telecommunications, as well as charting the efforts of technology companies to improve their inclusion and diversity strategies, a topic close to her heart.
Sabina has also held a number of editorial roles at Harper's Bazaar, Cube Collective, and HighClouds.
-
 Lenovo wows at MWC with concepts for a modular ThinkBook and desktop AI-devices
Lenovo wows at MWC with concepts for a modular ThinkBook and desktop AI-devicesNews A new modular ThinkBook AI PC from Lenovo is the star of the show, with a delightfully versatile proof of concept
-
 Salesforce targets telco gains with new agentic AI tools
Salesforce targets telco gains with new agentic AI toolsNews Telecoms operators can draw on an array of pre-built agents to automate and streamline tasks
-
 Windows 10 extended support costs could top $7 billion
Windows 10 extended support costs could top $7 billionNews Enterprises sticking with Windows 10 after the October deadline face huge costs
-
 Tiny11 review: Windows 11 with only 2GB of RAM
Tiny11 review: Windows 11 with only 2GB of RAMReview A version of Windows 11 for older machines that don't meet the full requirements
-
 Red Hat Enterprise Linux becomes foundational operating system for Cohesity Data Cloud
Red Hat Enterprise Linux becomes foundational operating system for Cohesity Data CloudNews New strategic partnership between Red Hat and Cohesity aims to drive innovation in the data security and management space
-
 Ubuntu shifts to four-week update cycle
Ubuntu shifts to four-week update cycleNews Critical fixes will also come every two weeks, mitigating the issues involved with releasing prompt patches on the old three-week cadence
-
 AlmaLinux follows Oracle in ditching RHEL compatibility
AlmaLinux follows Oracle in ditching RHEL compatibilityNews Application binary compatibility is now the aim with 1:1 now dropped
-
 How big is the Windows 10 cliff-edge?
How big is the Windows 10 cliff-edge?ITPro Network With some comparing the upcoming Windows 10 end of life to Windows XP, we ask members of the ITPro Network for their insight
-
 Everything you need to know about the latest Windows 11 updates - from bug fixes to brand-new features
Everything you need to know about the latest Windows 11 updates - from bug fixes to brand-new featuresNews Two new cumulative updates are on the way and will be installed automatically on Windows 10 and Windows 11 machines
-
 How to download a Windows 11 ISO file and perform a clean install
How to download a Windows 11 ISO file and perform a clean installTutorial Use a Windows 11 ISO to install the operating system afresh
