How to check if you’ve been affected by Salesforce attacks – and stop hackers dead in their tracks
The FBI has detailed steps enterprises can take to prevent falling victim to Salesforce attacks


The FBI has issued a FLASH alert over the threat posed to enterprises by threat groups targeting Salesforce environments.
According to the law enforcement agency, two threat groups, tracked as UNC6040 and UNC6395, have ramped up targeting of Salesforce customers amidst a spate of attacks in recent months.
“Both groups have recently been observed targeting organizations' Salesforce platforms via different initial access mechanisms,” the FBI said in its advisory.
30% off Keeper Security's Business Starter and Business plans
Keeper Security is trusted and valued by thousands of businesses and millions of employees. Why not join them and protect your most important assets while taking advantage of this special offer?
The agency added it had released information to “maximize awareness” and provide indicators of compromise (IOCs) commonly associated with attacks by these groups.
So what should enterprises be looking out for?
How both groups are targeting Salesforce customers
According to the FBI, UNC6040 has been targeting Salesforce customers since October 2024, typically gaining initial access through social engineering techniques.
These include ‘vishing’ (voice-based phishing) attacks to dupe users into granting access to Salesforce accounts.
Sign up today and you will receive a free copy of our Future Focus 2025 report - the leading guidance on AI, cybersecurity and other IT challenges as per 700+ senior executives
“UNC6040 threat actors commonly call victims’ call centers posing as IT support employees addressing enterprise-wide connectivity issues,” the advisory notes.
“Under the guise of closing an auto-generated ticket, UNC6040 actors trick customer support employees into taking actions that grant the attackers access or lead to the sharing of employee credentials, allowing them access to targeted companies’ Salesforce instances to exfiltrate customer data.”
During these attacks, threat actors have used ‘phishing panels’, directing victims to phony login pages which record login details and ultimately give the hackers access.
“UNC6040 threat actors have also directly requested user credentials and multifactor authentication codes to authenticate and add the Salesforce Data Loader application, facilitating data exfiltration,” the advisory added.
Meanwhile, UNC6395 has been observed using a different method, capitalizing on compromised OAuth tokens for the Salesloft Drift application.
“Using the compromised OAuth tokens and third-party app integration, UNC6395 threat actors were able to compromise victims’ Salesforce instances and exfiltrate data,” the FBI noted.
A host of organizations globally have been impacted by Salesloft Drift breaches in recent months, with Google, Zscaler, Palo Alto Networks, and Cloudflare all revealing they’ve fallen victim.
Salesloft has since revoked active access and refresh tokens for Drift, preventing threat actors from accessing victims’ Salesforce platforms connected to the app.
How to know if you’ve been hit and what to do
In terms of IOCs, the FBI has detailed a list of IPs associated with both groups, with UNC6040 commanding the lion’s share. The agency recommends enterprises “investigate and vet indicators prior to taking action, such as blocking”.
A full list of UNC6040 IPs can be found below.
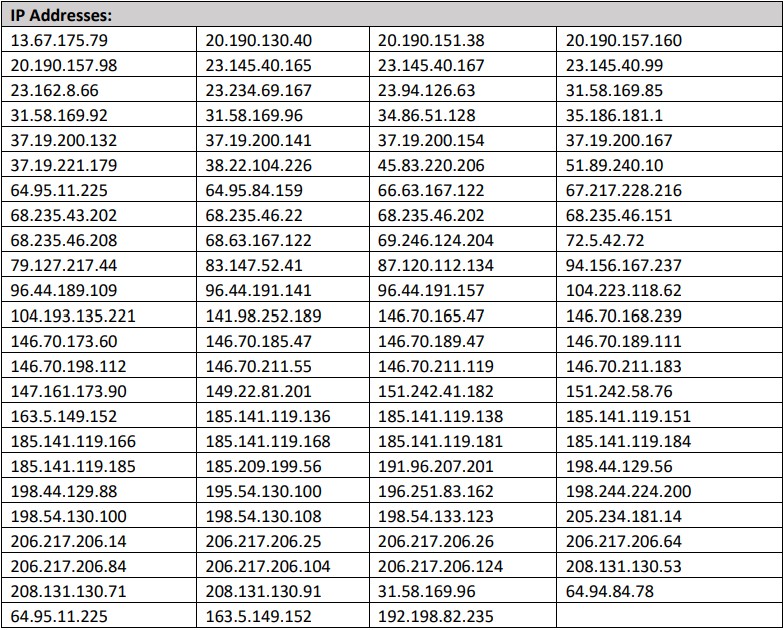
To mitigate the threat posed by these groups, the FBI also recommended a series of steps enterprises can take.
First and foremost, this includes training call center employees to recognize and report phishing attempts alongside implementation of MFA for “as many services as possible”.
Elsewhere, enterprises should implement authentication, authorization, and accounting (AAA) systems to “limit actions users can perform”.
“Apply the Principle of Least Privilege to user accounts and groups, allowing only the performance of authorized actions,” the agency said.
Other tips from the FBI include:
- Enforcement of IP-based access restrictions and monitoring of API usage.
- Monitoring network logs and browser session for anomalous activity and indicators of data exfiltration.
- Conduct reviews of third-party integrations connected to third-party software instances.
Make sure to follow ITPro on Google News to keep tabs on all our latest news, analysis, and reviews.
MORE FROM ITPRO
- Jaguar Land Rover u-turns on cyber attack containment claims, admits ‘some data has been affected’
- LNER warns customers to remain vigilant after personal data exposed in cyber attack
- FBI warns 'indiscriminate' Salt Typhoon hacking campaign has hit organizations in more than 80 countries

Ross Kelly is ITPro's News & Analysis Editor, responsible for leading the brand's news output and in-depth reporting on the latest stories from across the business technology landscape. Ross was previously a Staff Writer, during which time he developed a keen interest in cyber security, business leadership, and emerging technologies.
He graduated from Edinburgh Napier University in 2016 with a BA (Hons) in Journalism, and joined ITPro in 2022 after four years working in technology conference research.
For news pitches, you can contact Ross at ross.kelly@futurenet.com, or on Twitter and LinkedIn.
-
 Will autonomous robotics leap forward in 2026?
Will autonomous robotics leap forward in 2026?In-depth Connectivity and cost benefits remain barriers, despite breakthroughs in physical AI
-
 AWS and NTT Data team up to drive legacy IT modernization in Europe
AWS and NTT Data team up to drive legacy IT modernization in EuropeNews Partnership between AWS and NTT DATA aims to boost AWS European Sovereign Cloud capabilities
-
 90% of companies are woefully unprepared for quantum security threats – analysts say they need to get a move on
90% of companies are woefully unprepared for quantum security threats – analysts say they need to get a move onNews Quantum security threats are coming, but a Bain & Company survey shows systems aren't yet in place to prevent widespread chaos
-
 LastPass issues alert as customers targeted in new phishing campaign
LastPass issues alert as customers targeted in new phishing campaignNews LastPass has urged customers to be on the alert for phishing emails amidst an ongoing scam campaign that encourages users to backup vaults.
-
 NCSC names and shames pro-Russia hacktivist group amid escalating DDoS attacks on UK public services
NCSC names and shames pro-Russia hacktivist group amid escalating DDoS attacks on UK public servicesNews Russia-linked hacktivists are increasingly trying to cause chaos for UK organizations
-
 An AWS CodeBuild vulnerability could’ve caused supply chain chaos – luckily a fix was applied before disaster struck
An AWS CodeBuild vulnerability could’ve caused supply chain chaos – luckily a fix was applied before disaster struckNews A single misconfiguration could have allowed attackers to inject malicious code to launch a platform-wide compromise
-
 There’s a dangerous new ransomware variant on the block – and cyber experts warn it’s flying under the radar
There’s a dangerous new ransomware variant on the block – and cyber experts warn it’s flying under the radarNews The new DeadLock ransomware family is taking off in the wild, researchers warn
-
 Supply chain and AI security in the spotlight for cyber leaders in 2026
Supply chain and AI security in the spotlight for cyber leaders in 2026News Organizations are sharpening their focus on supply chain security and shoring up AI systems
-
 Veeam patches Backup & Replication vulnerabilities, urges users to update
Veeam patches Backup & Replication vulnerabilities, urges users to updateNews The vulnerabilities affect Veeam Backup & Replication 13.0.1.180 and all earlier version 13 builds – but not previous versions.
-
 NHS supplier DXS International confirms cyber attack – here’s what we know so far
NHS supplier DXS International confirms cyber attack – here’s what we know so farNews The NHS supplier says front-line clinical services are unaffected
