Leading malware campaigns are abusing genuine Windows shortcuts to bypass Microsoft's VBA macro block
The likes of Emotet and Qakbot, as well as Russia-linked state-sponsored hackers, have all pivoted to the new infection technique


A number of the world’s most pervasive malware campaigns have switched infection tactics after Microsoft blocked VBA macros by default.
The likes of Emotet and Qakbot have both been observed abusing Windows Explorer and LNK files as an alternative infection exploit, from the second quarter of 2022 onwards.
Microsoft's ban on VBA macros in February was welcomed almost universally, and was considered a long-overdue move from the company in light of cyber attackers having abused the feature to distribute malware for years.
Blocking VBA macros meant Microsoft prevented the execution of commands from untrusted sources such as an Excel document downloaded from an email, so hackers have pivoted to abusing trusted contexts like Windows Explorer instead, the researchers said.
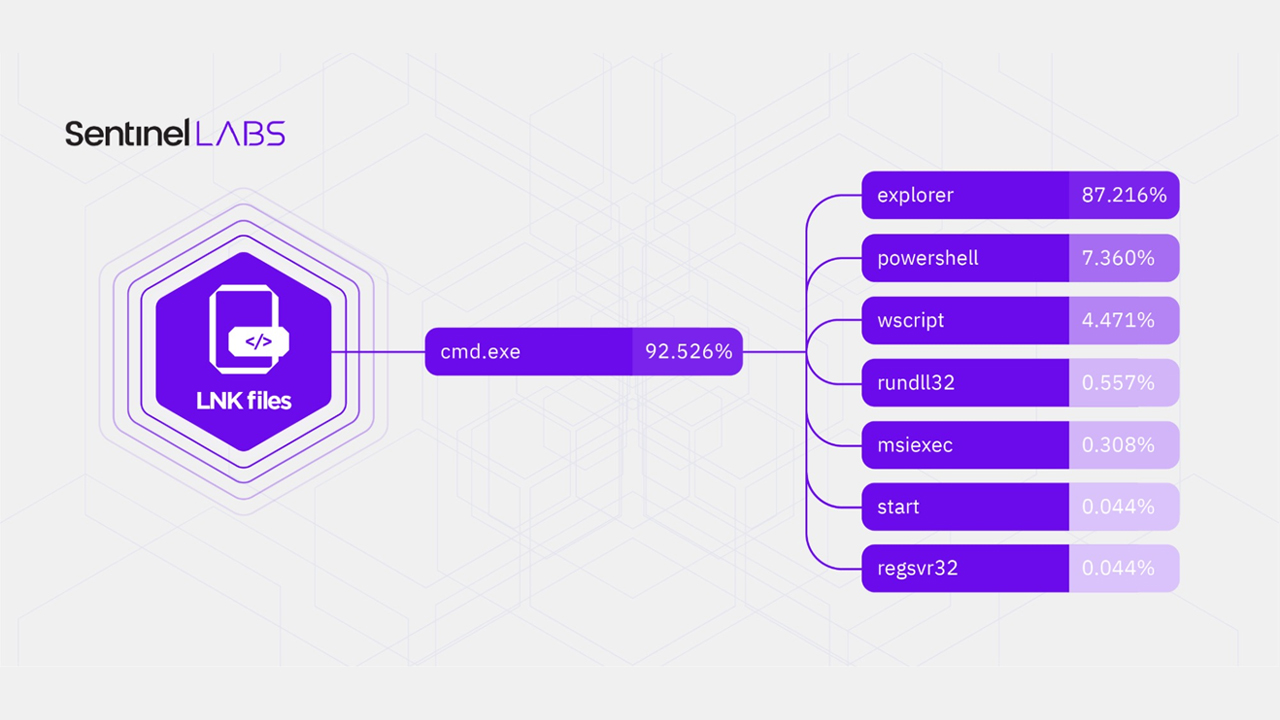
Windows Explorer is the most popular living-off-the-land binary (LOLbin) abused in these types of attacks, Sentinel Labs researchers said, and attackers are abusing it to distribute malicious Windows shortcut files (LNK files).
Windows Explorer was the most-abused LOLbin by far, according to the cyber security company’s figures, with 87.2% prevalence. This was followed by Powershell at 7.3%, then Windows Script Host (wscript) at 4.4%, and rundll32 at 0.5%.
A total of 27,510 malicious LNK samples were analysed from open source security intelligence platform VirusTotal, the company said, and research co-author said a surprising observation was that Microsoft Malware Protection Engine (msmpeng) wasn’t more widely abused.
Sign up today and you will receive a free copy of our Future Focus 2025 report - the leading guidance on AI, cybersecurity and other IT challenges as per 700+ senior executives
MsMpEng has previously been used by the likes of the now-shuttered REvil ransomware operation in its supply chain attack on Kaseya to side-load malware.
In almost all of the malicious LNK samples that were analysed (92,526%), Windows Command prompt was the target which then executed Windows commands and/or attacker-provided files.
These commands typically spanned tasks like flow control, file manipulation, executing attacker-supplied code in LOLbins like Explorer, information gathering and reconnaissance, and controlling the output of the command interpreter.
The shift towards LNK files over VBA macros is a relatively new one, but one that’s being made by many threat actors.
Sentinel Labs said tools like NativeOne’s mLNK tool, a malicious LNK generator, have been released recently to help cyber criminals more easily create LNK-abusing malware campaigns.
QuantumBuilder is another tool that’s similar to mLNK that features an intuitive user interface. Advertising campaigns for this tool first surfaced in May 2022, the researchers said.
Additionally, Russian state-sponsored cyber criminals have been found abusing the brand-new penetration testing tool Brute Ratel C4. The latest red teaming tool to gain popularity has been dubbed ‘the next Cobalt Strike’ and also uses LNK files to infect victims with malware.
In March, Google Threat Analysis Group (TAG) identified initial access broker (IAB) Exotic Lily using LNK shortcuts to drop malicious ISO files in ransomware-for-hire campaigns.
The new tools and techniques have all surfaced after Microsoft first announced that it would block VBA macros by default. Since then, it temporarily backtracked on the decision, but recently said they will be blocked for good.

Connor Jones has been at the forefront of global cyber security news coverage for the past few years, breaking developments on major stories such as LockBit’s ransomware attack on Royal Mail International, and many others. He has also made sporadic appearances on the ITPro Podcast discussing topics from home desk setups all the way to hacking systems using prosthetic limbs. He has a master’s degree in Magazine Journalism from the University of Sheffield, and has previously written for the likes of Red Bull Esports and UNILAD tech during his career that started in 2015.
-
 What is Microsoft Maia?
What is Microsoft Maia?Explainer Microsoft's in-house chip is planned to a core aspect of Microsoft Copilot and future Azure AI offerings
-
 If Satya Nadella wants us to take AI seriously, let’s forget about mass adoption and start with a return on investment for those already using it
If Satya Nadella wants us to take AI seriously, let’s forget about mass adoption and start with a return on investment for those already using itOpinion If Satya Nadella wants us to take AI seriously, let's start with ROI for businesses
-
 Google pays largest-ever bug bounty worth £500,000
Google pays largest-ever bug bounty worth £500,000News The company remained tight-lipped over the exploit itself, but speculation is possible given its publicly available rewards breakdown
-
 OpenSSL 3.0 vulnerability: Patch released for security scare
OpenSSL 3.0 vulnerability: Patch released for security scareNews The severity has been downgraded from 'critical' to 'high' and comparisons to Heartbleed have been quashed
-
 Hacker steals $566 million from Binance Bridge using proof-forgery exploit
Hacker steals $566 million from Binance Bridge using proof-forgery exploitNews An exploit discovered in the exchange platform's proof verifier let the hacker take 2m BNB without raising alarm bells
-
 CISA issues fresh orders to polish security vulnerability detection in federal agencies
CISA issues fresh orders to polish security vulnerability detection in federal agenciesNews The move marks the latest step in the cyber security authority's ongoing ambition to minimise the government's exposure to attacks
-
 Mozilla patches high-severity security flaws in new ‘speedy’ Firefox release
Mozilla patches high-severity security flaws in new ‘speedy’ Firefox releaseNews Numerous vulnerabilities across Mozilla's products could potentially lead to code execution and system takeover
-
 WordPress plugin vulnerability leaves sites open to total takeover
WordPress plugin vulnerability leaves sites open to total takeoverNews Customers on WordFence's paid tiers will get protection from the WPGate exploit right away, but those on the free-tier face a 30-day delay
-
 Numerous HP business laptops and desktops vulnerable to publicly disclosed security bugs
Numerous HP business laptops and desktops vulnerable to publicly disclosed security bugsNews Researchers revealed the details of the six vulnerabilities at Black Hat in August but many laptops, desktops, and workstations remain vulnerable
-
 HP patches high-severity security flaw in its own support tool
HP patches high-severity security flaw in its own support toolNews The application that's installed in every HP desktop and notebook was allowing hackers to elevate privileges through a DLL hijacking vulnerability