Ransomware activity down 11% worldwide in Q3, but rise expected
LockBit increased its share of the landscape even as attacks declined, while new groups have capitalised on the fall of Conti


Sign up today and you will receive a free copy of our Future Focus 2025 report - the leading guidance on AI, cybersecurity and other IT challenges as per 700+ senior executives
You are now subscribed
Your newsletter sign-up was successful
A new report has found that global ransomware activity dropped throughout the third quarter as the order of dominant groups in the landscape shifted, but that businesses should expect a surge by threat actors in Q4 to exploit consumer trends.
RELATED RESOURCE

How to reduce the risk of phishing and ransomware
Top security concerns and tips for mitigation
The number of ransomware attacks in Q3 2022 was down 10.5% on Q2, according to the latest report by cyber security firm Digital Shadows. This was driven in part by the sudden cessation of activity by the Conti group, as well as a reorganisation of leading groups over July and August.
LockBit 3.0, the latest strain by the LockBit group of threat actors, consolidated its lead across the landscape in Q3, accounting for 35.1% of all activity across the period, compared to 32.8% in Q2. The group's rise, even as its overall activity declined, has been matched by the growth of a number of new groups, including Black Basta, Hive Leaks, and Alphv, which account for 9%, 8%, and 7% of activity respectively.
Digital Shadows suggests that these groups have directly taken advantage of the gap in the market left by Conti, which after threatening to overthrow the Costa Rican government in May, apparently shut down in June. The group’s website has disappeared, and a drop off in activity right at the end of Q2 has been linked directly to the group’s apparent cessation of attacks.
Groups that bucked the trend with increased activity across the period include ‘AvosLocker’ (up 50%) and Hive Leaks (up 80.8%). The latter operates the Hive payload, which was singled out by Microsoft in Q3 for its sophisticated functions, and for being written in the programming language Rust, which is becoming a popular programming language for hacker groups.
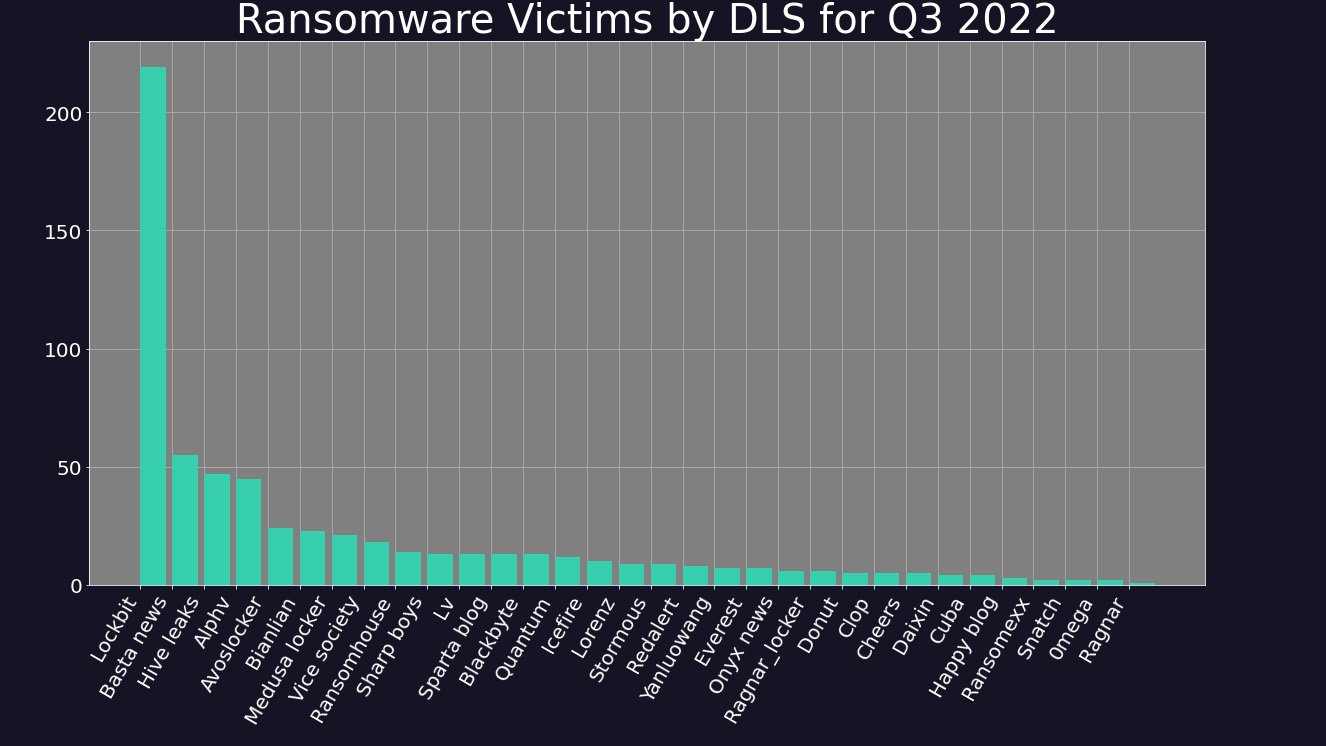
Some within the cyber security community have suggested that Hive is composed of former Conti actors, or is even a continuation of the same group. Investigative journalist and cyber crime expert Brian Krebs tweeted that attacks on Costa Rica appeared to have been committed by Hive, but that “with Conti apparently in the process of rebranding, it could just as well be the same criminals involved.”
However, Emisoft threat analyst Brett Callow subsequently tweeted a screenshot from Hive’s website that states “we are not related with Conti”. No evidence yet links any emerging group with Conti.
Sign up today and you will receive a free copy of our Future Focus 2025 report - the leading guidance on AI, cybersecurity and other IT challenges as per 700+ senior executives
Around 39% of all attacks across Q3 were made against victims within the United States, reflective of the consolidation of wealthy companies within the country. France and Spain followed, with the UK the fourth most targeted in the same period, accounting for 4.8% of victims. This marks a fall from the UK’s third place in Q2, and appears to have been driven by a surge in attacks in France and Spain, including Hive's attack on French telco giant Altice in August.
Indeed, while almost all countries saw decreased ransomware attacks in Q3, France, Spain and Israel saw rises. Spain was an outlier, with a 66% rise in ransomware activity across the quarter tied to a surge by the group ‘Sparta Blog.’
The industrial goods and services sector remained the most targeted sector throughout the period, recording nearly double the attacks of the technology sector, the next most targeted. As the war in Ukraine drags on, attacks on supply chains and critical national infrastructure (CNI) continue to rise, and state-backing of ransomware attacks will continue to increase such action.
Bracing for a rise in Q4
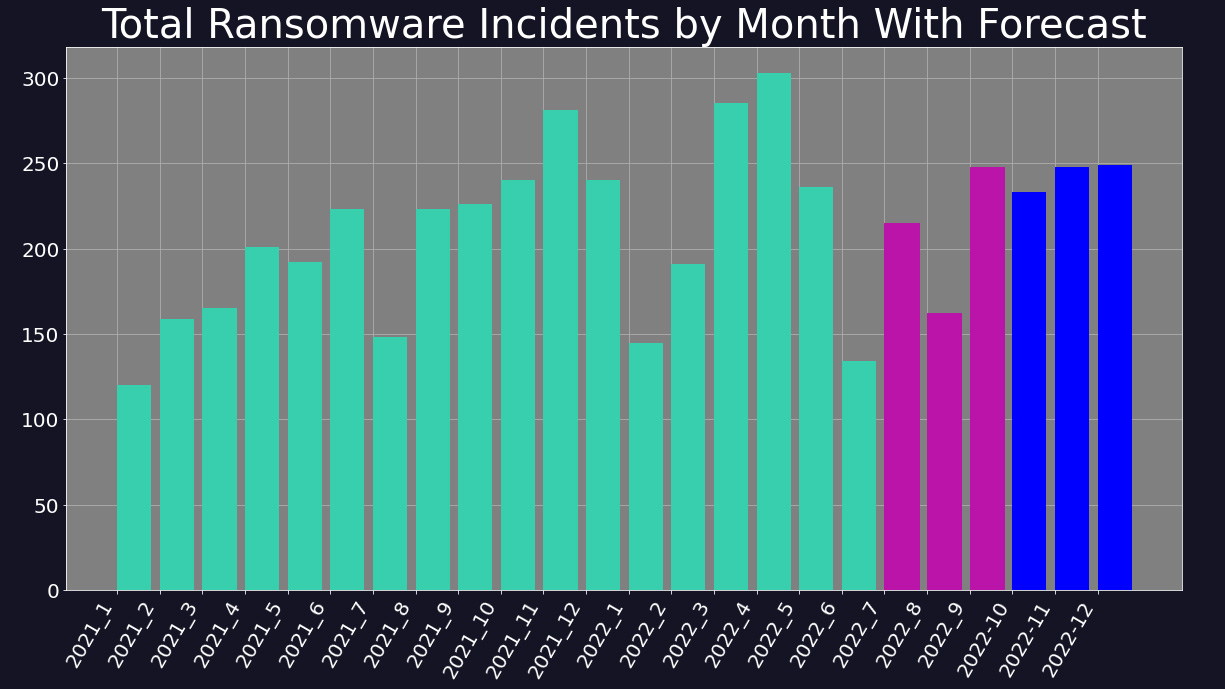
Digital Shadows forecasts a rise in activity in Q4 2022. This is not unusual, as commercial events such as Black Friday and Cyber Monday often coincide with an increase in malicious activity online, while online shopping around Christmas is exploited by threat actors with phishing campaigns.
After falling prey to a distributed denial of service (DDoS) attack in August, which took down its website for several days, the LockBit group vowed to be ‘more aggressive’ and stated that it was recruiting new members. This may be linked to the increase of attacks at the end of Q3, and indeed the LockBit group saw its highest ever share of international ransomware activity at 40%.
Concerns have also been raised due to the alleged leak of a LockBit 3.0 ‘builder’ in September. If legitimate, this would allow rival threat actors to create their own version of LockBit ransomware, and as such the leak could precede a spike in use of the highly-effective malware throughout Q4 and beyond.

Rory Bathgate is Features and Multimedia Editor at ITPro, overseeing all in-depth content and case studies. He can also be found co-hosting the ITPro Podcast with Jane McCallion, swapping a keyboard for a microphone to discuss the latest learnings with thought leaders from across the tech sector.
In his free time, Rory enjoys photography, video editing, and good science fiction. After graduating from the University of Kent with a BA in English and American Literature, Rory undertook an MA in Eighteenth-Century Studies at King’s College London. He joined ITPro in 2022 as a graduate, following four years in student journalism. You can contact Rory at rory.bathgate@futurenet.com or on LinkedIn.
-
 Poor workplace communication is confusing your colleagues and destroying productivity
Poor workplace communication is confusing your colleagues and destroying productivityNews Engaging with colleagues via email or chat platforms wastes time and hampers team alignment
-
 How the Cybersecurity and Resilience Bill could impact MSPs
How the Cybersecurity and Resilience Bill could impact MSPsIndustry Insights With the Cybersecurity and Resilience Bill now in Parliament, how should MSPs prepare for heightened regulatory scrutiny?
-
 Ransomware gangs are using employee monitoring software as a springboard for cyber attacks
Ransomware gangs are using employee monitoring software as a springboard for cyber attacksNews Two attempted attacks aimed to exploit Net Monitor for Employees Professional and SimpleHelp
-
 Ransomware gangs are sharing virtual machines to wage cyber attacks on the cheap – but it could be their undoing
Ransomware gangs are sharing virtual machines to wage cyber attacks on the cheap – but it could be their undoingNews Thousands of attacker servers all had the same autogenerated Windows hostnames, according to Sophos
-
 Google issues warning over ShinyHunters-branded vishing campaigns
Google issues warning over ShinyHunters-branded vishing campaignsNews Related groups are stealing data through voice phishing and fake credential harvesting websites
-
 The FBI has seized the RAMP hacking forum, but will the takedown stick? History tells us otherwise
The FBI has seized the RAMP hacking forum, but will the takedown stick? History tells us otherwiseNews Billing itself as the “only place ransomware allowed", RAMP catered mainly for Russian-speaking cyber criminals
-
 Everything we know so far about the Nike data breach
Everything we know so far about the Nike data breachNews Hackers behind the WorldLeaks ransomware group claim to have accessed sensitive corporate data
-
 There’s a dangerous new ransomware variant on the block – and cyber experts warn it’s flying under the radar
There’s a dangerous new ransomware variant on the block – and cyber experts warn it’s flying under the radarNews The new DeadLock ransomware family is taking off in the wild, researchers warn
-
 Hacker offering US engineering firm data online after alleged breach
Hacker offering US engineering firm data online after alleged breachNews Data relating to Tampa Electric Company, Duke Energy Florida, and American Electric Power was allegedly stolen
-
 Cybersecurity experts face 20 years in prison following ransomware campaign
Cybersecurity experts face 20 years in prison following ransomware campaignTwo men used their tech expertise to carry out ALPHV BlackCat ransomware attacks