Businesses on alert as mobile malware surges 500%
Researchers say hackers are deploying new tactics that put Android and iOS at equal risk


Sign up today and you will receive a free copy of our Future Focus 2025 report - the leading guidance on AI, cybersecurity and other IT challenges as per 700+ senior executives
You are now subscribed
Your newsletter sign-up was successful
Researchers have said they observed a 500% increase in mobile malware infections across Europe since the start of February 2022.
The majority of malware was observed on Android devices, with six of the most serious strains targeting Google's operating system compared to just one targeting iOS, according to Proofpoint researchers.
Following an uptick in mobile malware infections back in April 2021, researchers told IT Pro that detections had largely tapered off and remained low until February 2022, although they were unable to pinpoint a reason for the sudden surge.
Proofpoint said most mobile malware is still downloaded via app stores and is especially prevalent on Android devices given the platform’s openness to multiple different app stores.
Side-loading – the practice of allowing apps to be installed via third-party app stores or directly onto the device – is also prohibited on iOS, helping to limit the spread of infections.
However, Proofpoint said it has noticed a distinct rise in attacks using mobile messaging, including SMS-based phishing attacks known as smishing. Given Android’s support for side-loading, it means this technique is more effective on that platform compared to iOS.
The finding is especially important for businesses that distribute Android-based company devices to their workforce. Many businesses install security measures that prevent access to third-party app stores but smishing may bypass some of these provisions.
Sign up today and you will receive a free copy of our Future Focus 2025 report - the leading guidance on AI, cybersecurity and other IT challenges as per 700+ senior executives
“Mobile messaging is a highly trusted communication channel and users are much more apt to read and access links/URLs contained in mobile messages than those in email,” said Jacinta Tobin, vice president of Cloudmark operations at Proofpoint to IT Pro.
RELATED RESOURCE

Introducing the zero trust edge model for security and network services
Get a better understanding of emerging zero trust solutions
“This level of trust combined with the reach of mobile devices in the general public, where nine in ten possess a mobile device, makes mobile messaging a very attractive platform for commercial and marketing activity. This makes the mobile channel ripe for fraud and identity theft both now and in the future through this expansion.”
The most common types of malware found were those that used malicious apps to record phone calls, or those that take audio from the device outside of phone calls.
Data wipers, which have been especially common in the recent cyber attacks on Ukraine emanating from Russia, were also increasing in popularity.
This differs from the traditional purpose of malware, Proofpoint said, which typically involves gaining access to a system and potentially stealing data or account credentials.
Of the most common malware types, all had a financial impersonation component and all had a credential-stealing function.
For example, the long-feared FluBot malware, which installs an invisible overlay on mobiles to steal login credentials, activated when banking apps are used, was found to be one of the most common types of malware affecting Android users in Europe.
TangleBot was first observed in North America but has recently been found in Turkey. It typically spreads via fraudulent package-delivery notifications and may have links to the FluBot campaign. Notably, it is one of the few malware strains that combine financial impersonation with the newer audio-recording thefts.
“In both cases, the malware uses similar distribution methodologies, landing pages, language and SMS lures,” Proofpoint said. “One enticing lure that TangleBot has been known to use is a software update notification.”
Proofpoint said “awareness is critical” when keeping safe online, and more needs to be known about the dangers of mobile malware.
Users have been advised to be extra vigilant when it comes to reviewing emails and texts, especially for Android users, and consider installing a mobile antivirus app from a trusted source.
“Consumers need to be very sceptical of mobile messages that come from unknown sources,” said Tobin. “And it’s important to never click on links in text messages, no matter how realistic they look.
“If you want to contact the purported vendor sending you a link, do so directly through their website and always manually enter the web address/URL. For offer codes, type them directly into the site as well. It’s also vital that you don’t respond to strange texts or texts from unknown sources. Doing so will often confirm you’re a real person to future scammers.”

Connor Jones has been at the forefront of global cyber security news coverage for the past few years, breaking developments on major stories such as LockBit’s ransomware attack on Royal Mail International, and many others. He has also made sporadic appearances on the ITPro Podcast discussing topics from home desk setups all the way to hacking systems using prosthetic limbs. He has a master’s degree in Magazine Journalism from the University of Sheffield, and has previously written for the likes of Red Bull Esports and UNILAD tech during his career that started in 2015.
-
 Mobile app security is a huge blind spot for developer teams – 93% are confident their applications are secure, but 62% reported breaches last year
Mobile app security is a huge blind spot for developer teams – 93% are confident their applications are secure, but 62% reported breaches last yearNews Organizations are overconfident about their mobile app security practices, according to new research, and it’s putting enterprises and consumers alike at risk.
-
 APIs: Understanding the business benefits and risks
APIs: Understanding the business benefits and riskswhitepaper What you need to know about potential data exposure from APIs
-
 Apple patches actively exploited iPhone, iPad zero-day and 18 other security flaws
Apple patches actively exploited iPhone, iPad zero-day and 18 other security flawsNews The out-of-bounds write error is the eighth actively exploited zero-day impacting Apple hardware this year and could facilitate kernel-level code execution
-
 Qualcomm and Mediatek flaws left millions of Android users at risk
Qualcomm and Mediatek flaws left millions of Android users at riskNews An open source audio codec used by chipset firms is believed to have put two-thirds of Android users' private calls and files at risk
-
 Apple fixes array of iOS, macOS zero-days and code execution security flaws
Apple fixes array of iOS, macOS zero-days and code execution security flawsNews The first wave of security updates for Apple products in 2022 follows a year in which a wide variety of security flaws plagued its portfolio of devices
-
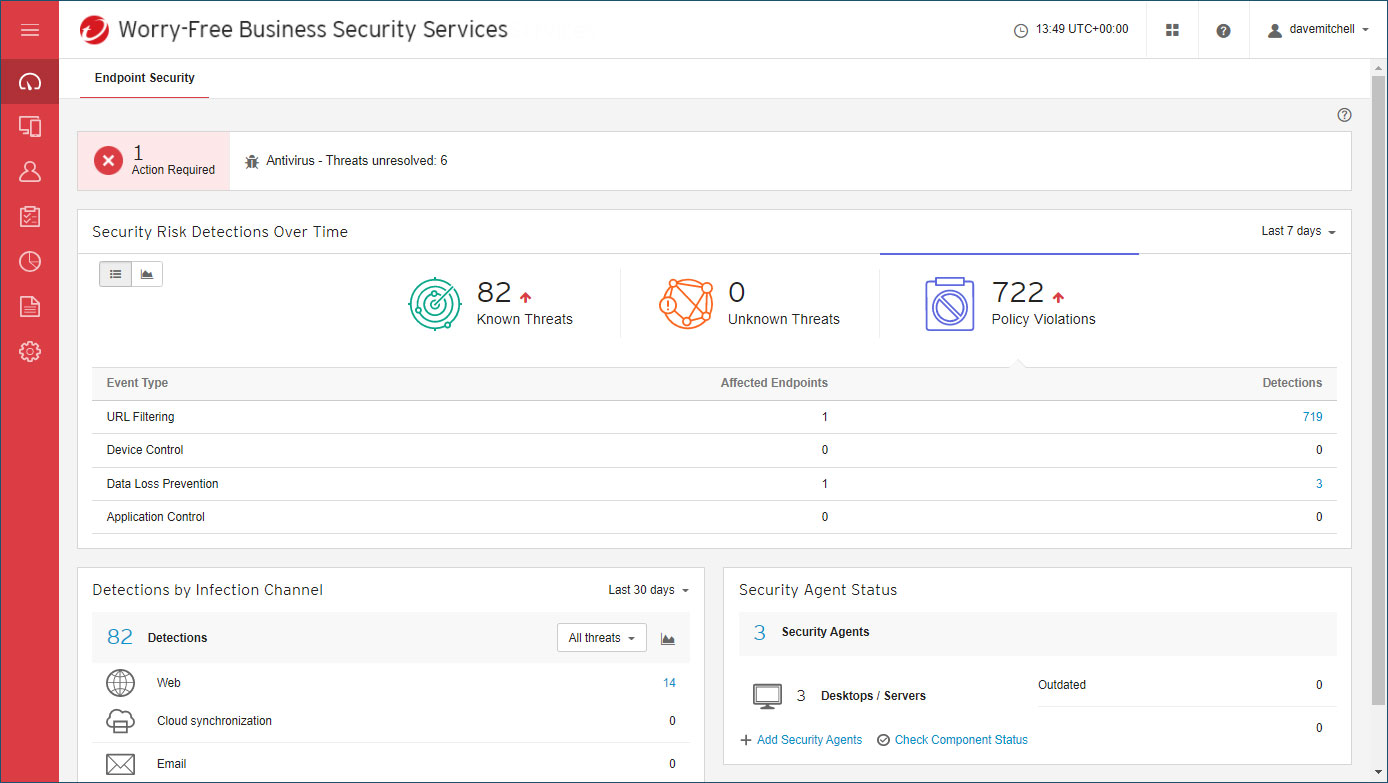 Trend Micro Worry-Free Business Security review: Great cloud-managed malware protection
Trend Micro Worry-Free Business Security review: Great cloud-managed malware protectionReviews A reassuringly simple endpoint-protection solution – although mobile support is basic
-
 Over 300,000 Android users downloaded banking trojan malware
Over 300,000 Android users downloaded banking trojan malwareNews Hackers defeated Google Play restrictions by using smaller droppers in apps and eliminating permissions needed
-
 Flaw in Android phones could let attackers eavesdrop on calls
Flaw in Android phones could let attackers eavesdrop on callsNews The vulnerable chips are thought to be present in 37% of all smartphones worldwide

