Microsoft says skip SMS and voice multi-factor authentication
Firm argues some forms of MFA are vulnerable to social engineering attacks

Microsoft is warning businesses against using multi-factor authentication (MFA) systems that rely on voice and SMS due to security concerns.
In a blog post, Microsoft director of identity security Alex Weinert provides a range of reasons why businesses should avoid SMS and voice MFA.
“These mechanisms are based on publicly switched telephone networks (PSTN), and I believe they’re the least secure of the MFA methods available today,” Weinert writes. “That gap will only widen as MFA adoption increases attackers’ interest in breaking these methods and purpose-built authenticators extend their security and usability advantages.”
Lack of encryption
What’s particularly problematic with SMS and voice-based MFA is they use no encryption, making it easy for hackers to intercept them, according to Weinert.
“From a practical usability perspective, we can’t overlay encryption onto these protocols because users would be unable to read them (there are other reasons too, like message bloat, which have prevented these from taking hold over the existing protocols)”
“What this means is that signals can be intercepted by anyone who can get access to the switching network or within the radio range of a device.”
Social engineering
Weinert also believes SMS and voice-based MFA are more susceptible to social engineering techniques. In particular, he says customer support agents are “vulnerable to charm, coercion, bribery, or extortion.” With those tactics, perpetrators could trick customer support representatives into providing “access to the SMS or voice channel.”
Sign up today and you will receive a free copy of our Future Focus 2025 report - the leading guidance on AI, cybersecurity and other IT challenges as per 700+ senior executives
Weinert adds, “While social engineering attacks impact email systems as well, the major email systems (e.g. Outlook, Gmail) have a more developed “muscle” for preventing account compromise via their support ecosystems. This leads to everything from message intercept, to call forwarding attacks, to SIM jacking.”
Performance issues
Another issue is that these systems can be affected by mobile operator performance, with Weinert explaining they “are not 100% reliable, and reporting is not 100% consistent.”
He also pointed out that evolving regulations make these techniques challenging. “Due to the increase in spam in SMS formats, regulators have required regulations on identifying codes, transmit rates, message content, permission to send, and response to messages like ‘STOP.’”
“Unfortunately, however, these regulations change rapidly and are inconsistent from region to region and can (and have) resulted in major delivery outages. More outages, more user frustration.”
Phishing threats
Furthermore, the lack of context in SMS and GSM communications makes phishing an even bigger threat to people who use these types of MFA.
Weinert says, “In practical terms, the text or voice mediums limit how much information can be communicated to a user – SMS carries 160 characters, 70 if not using GSM, and once we get into languages which require encoding, the practical limit without message splitting is only around half that.“
“Phishing is a serious threat vector, and we want to empower the user with as much context as possible (or, using Windows Hello or FIDO, make phishing impossible) – SMS and voice formats restrict our ability to deliver the context under which authentication is being requested.”
Jake Moore, a security specialist at ESET, believes SMS-based MFA isn’t as safe as physical security keys or app-based tokens.
He told ITPro, “SMS messages are easily hacked as they are not encrypted and are at risk of SIM swapping attacks. However, if this is the only option, then it is still better than not having any extra verification.”
“Authenticator apps should be one of the first apps you install on your device and be used with every account you own. To go one step further, hardware security tokens are even more secure as they cannot be used in sophisticated social engineering techniques.“
Nicholas Fearn is a freelance technology journalist and copywriter from the Welsh valleys. His work has appeared in publications such as the FT, the Independent, the Daily Telegraph, the Next Web, T3, Android Central, Computer Weekly, and many others. He also happens to be a diehard Mariah Carey fan. You can follow Nicholas on Twitter.
-
 Microsoft unveils Maia 200 accelerator, claiming better performance per dollar than Amazon and Google
Microsoft unveils Maia 200 accelerator, claiming better performance per dollar than Amazon and GoogleNews The launch of Microsoft’s second-generation silicon solidifies its mission to scale AI workloads and directly control more of its infrastructure
-
 Infosys expands Swiss footprint with new Zurich office
Infosys expands Swiss footprint with new Zurich officeNews The firm has relocated its Swiss headquarters to support partners delivering AI-led digital transformation
-
 Mobile app security is a huge blind spot for developer teams – 93% are confident their applications are secure, but 62% reported breaches last year
Mobile app security is a huge blind spot for developer teams – 93% are confident their applications are secure, but 62% reported breaches last yearNews Organizations are overconfident about their mobile app security practices, according to new research, and it’s putting enterprises and consumers alike at risk.
-
 APIs: Understanding the business benefits and risks
APIs: Understanding the business benefits and riskswhitepaper What you need to know about potential data exposure from APIs
-
 Apple patches actively exploited iPhone, iPad zero-day and 18 other security flaws
Apple patches actively exploited iPhone, iPad zero-day and 18 other security flawsNews The out-of-bounds write error is the eighth actively exploited zero-day impacting Apple hardware this year and could facilitate kernel-level code execution
-
 Qualcomm and Mediatek flaws left millions of Android users at risk
Qualcomm and Mediatek flaws left millions of Android users at riskNews An open source audio codec used by chipset firms is believed to have put two-thirds of Android users' private calls and files at risk
-
 Businesses on alert as mobile malware surges 500%
Businesses on alert as mobile malware surges 500%News Researchers say hackers are deploying new tactics that put Android and iOS at equal risk
-
 Apple fixes array of iOS, macOS zero-days and code execution security flaws
Apple fixes array of iOS, macOS zero-days and code execution security flawsNews The first wave of security updates for Apple products in 2022 follows a year in which a wide variety of security flaws plagued its portfolio of devices
-
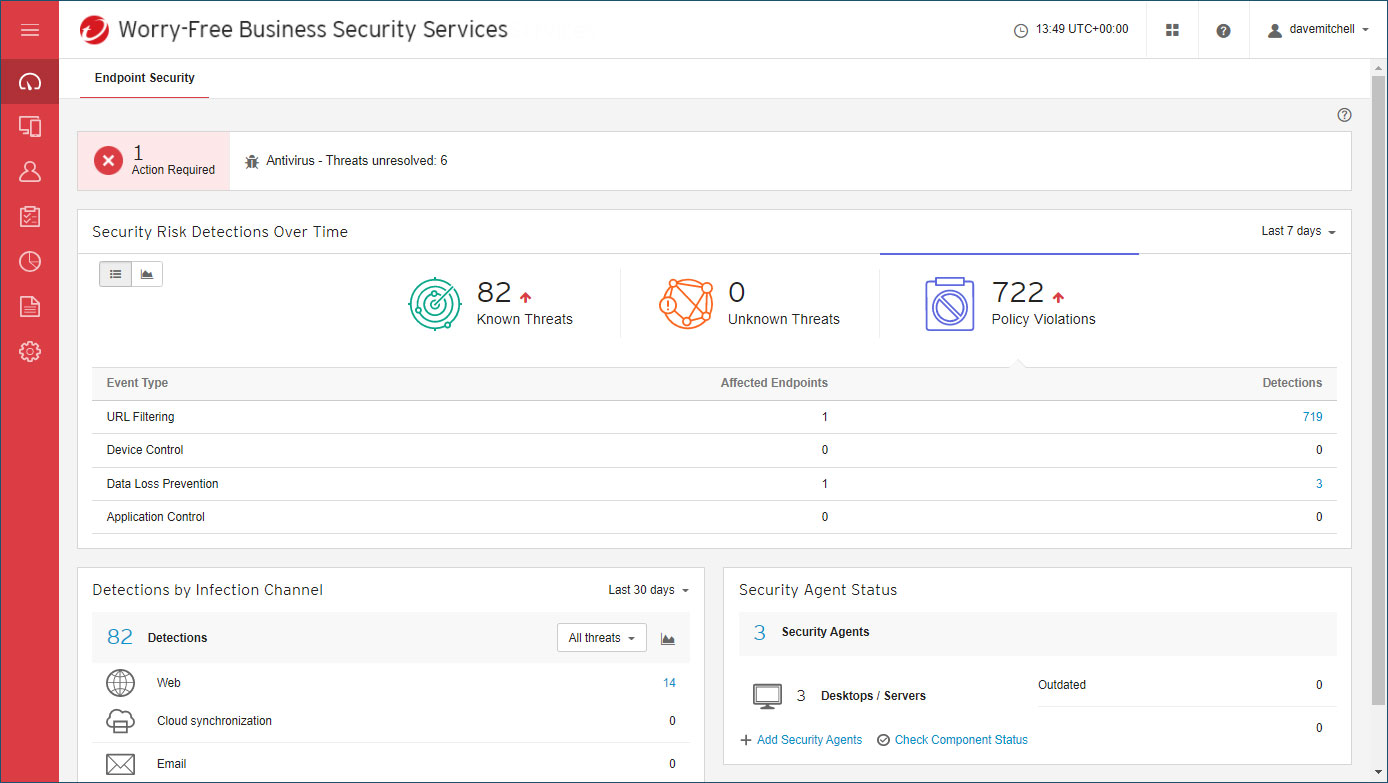 Trend Micro Worry-Free Business Security review: Great cloud-managed malware protection
Trend Micro Worry-Free Business Security review: Great cloud-managed malware protectionReviews A reassuringly simple endpoint-protection solution – although mobile support is basic
-
 Over 300,000 Android users downloaded banking trojan malware
Over 300,000 Android users downloaded banking trojan malwareNews Hackers defeated Google Play restrictions by using smaller droppers in apps and eliminating permissions needed