Eight Brits arrested over SIM swapping attacks on US celebs
International effort between UK and US law enforcement agencies takes down network of English and Scottish cyber criminals


Eight Brits have been arrested as part of an investigation into a series of 'SIM swapping' attacks across the US.
The men, aged between 18 and 26, are from England and Scotland and their arrests were part of an international effort with the National Crime Agency (NCA), the US Secret Service, Homeland Security, the FBI and the Santa Clara California District Attorney's Office.
The perpetrators are said to have illegally gained access to mobile phones belonging to US celebrities in order to steal large sums of money, either from their bank accounts or Bitcoin wallets, according to the NCA.
"This network targeted a large number of victims in the US and regularly attacked those they believed would be lucrative targets, such as famous sports stars and musicians," said NCA's head of operations Paul Creffield. "In this case, those arrested face prosecution for offences under the Computer Misuse Act, as well as fraud and money laundering as well as extradition to the USA for prosecution."
The criminals are accused of using a hack called 'SIM swapping' whereby they take over a victims phone number by deactivating the SIM and porting the allocated number over to a new one. This is often achieved by tricking mobile providers to swap the SIMs themselves, either using an insider or social engineering techniques.
Once they have control of the phone number, they use it to change the passwords on various apps and access contacts, emails and even bank details.
In the summer, a number of celebrities, such as Elon Musk and Barack Obama, had their Twitter accounts hacked via the same methods. Instagram, Twitter and a number of other social media platforms recently announced that they had disabled hundreds of accounts that were stolen through SIM swapping, citing the 'OGUsers' forum as the culprit for harvesting the usernames.
Sign up today and you will receive a free copy of our Future Focus 2025 report - the leading guidance on AI, cybersecurity and other IT challenges as per 700+ senior executives
Bobby Hellard is ITPro's Reviews Editor and has worked on CloudPro and ChannelPro since 2018. In his time at ITPro, Bobby has covered stories for all the major technology companies, such as Apple, Microsoft, Amazon and Facebook, and regularly attends industry-leading events such as AWS Re:Invent and Google Cloud Next.
Bobby mainly covers hardware reviews, but you will also recognize him as the face of many of our video reviews of laptops and smartphones.
-
 The UK AI revolution: navigating the future of the intelligent enterprise
The UK AI revolution: navigating the future of the intelligent enterpriseAs AI reshapes industries and societies, decision-makers in the UK face a critical choice: build a sovereign future or merely import it.
-
 Turning the UK AI revolution into a sovereign reality
Turning the UK AI revolution into a sovereign realityThe UK AI Revolution documentary series posed difficult questions about AI’s hype, control, and future. Now, IT leaders must find the architectural answers
-
 Mobile app security is a huge blind spot for developer teams – 93% are confident their applications are secure, but 62% reported breaches last year
Mobile app security is a huge blind spot for developer teams – 93% are confident their applications are secure, but 62% reported breaches last yearNews Organizations are overconfident about their mobile app security practices, according to new research, and it’s putting enterprises and consumers alike at risk.
-
 APIs: Understanding the business benefits and risks
APIs: Understanding the business benefits and riskswhitepaper What you need to know about potential data exposure from APIs
-
 Apple patches actively exploited iPhone, iPad zero-day and 18 other security flaws
Apple patches actively exploited iPhone, iPad zero-day and 18 other security flawsNews The out-of-bounds write error is the eighth actively exploited zero-day impacting Apple hardware this year and could facilitate kernel-level code execution
-
 Qualcomm and Mediatek flaws left millions of Android users at risk
Qualcomm and Mediatek flaws left millions of Android users at riskNews An open source audio codec used by chipset firms is believed to have put two-thirds of Android users' private calls and files at risk
-
 Businesses on alert as mobile malware surges 500%
Businesses on alert as mobile malware surges 500%News Researchers say hackers are deploying new tactics that put Android and iOS at equal risk
-
 Apple fixes array of iOS, macOS zero-days and code execution security flaws
Apple fixes array of iOS, macOS zero-days and code execution security flawsNews The first wave of security updates for Apple products in 2022 follows a year in which a wide variety of security flaws plagued its portfolio of devices
-
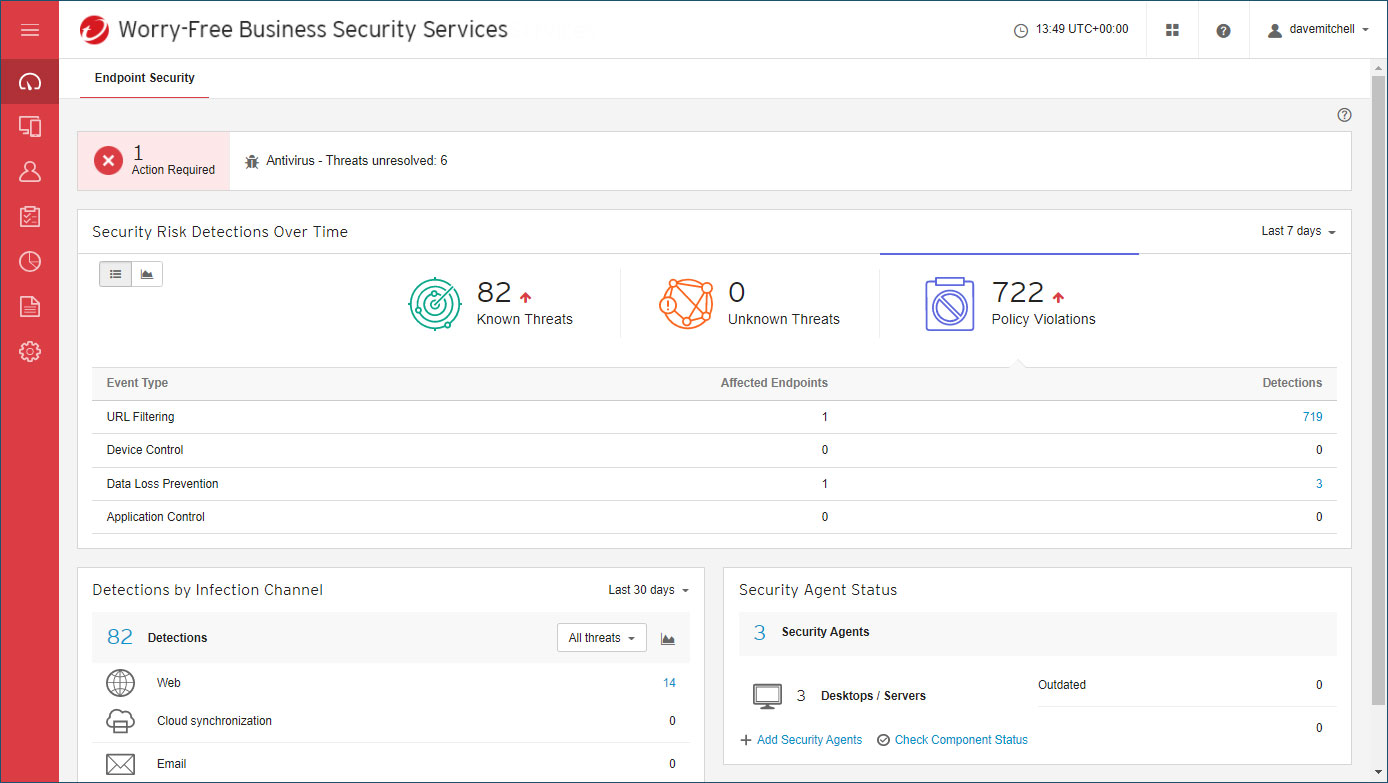 Trend Micro Worry-Free Business Security review: Great cloud-managed malware protection
Trend Micro Worry-Free Business Security review: Great cloud-managed malware protectionReviews A reassuringly simple endpoint-protection solution – although mobile support is basic
-
 Over 300,000 Android users downloaded banking trojan malware
Over 300,000 Android users downloaded banking trojan malwareNews Hackers defeated Google Play restrictions by using smaller droppers in apps and eliminating permissions needed
