Wormable Android malware is spreading through WhatsApp
The new strain poses as a Huawei app which users are tricked into downloading from a fake Google Play Store link


Android users are being warned against a wormable strain of malware that spreads itself by automatically replying to victims' WhatsApp messages with a malicious link.
The link this Android malware spreads through WhatsApp connects its victims with a convincing web page resembling Google’s Play Store, and a request to install a fake ‘Huawei Mobile’ app onto a user’s device.
This is according to ESET security researcher Lukas Stefanko, who published a short analysis of the malware’s mechanisms.
Should users install and activate the malicious app, it’ll immediately ask for various permissions to perform its key functions, including access to contacts and permission to draw over other apps. This latter feature means it can run in the background while other apps are in use on the victim’s device.
Users are also presented with a request to ignore battery optimisation, which if activated, means the app cannot be killed by the system if spare resources are needed.
Finally, the malicious app demands access to notifications, specifically WhatsApp notifications, so it can scan for incoming messages and distribute further among contacts.
Once all the permissions are guaranteed and the malicious app is set up, it runs in the background and waits for instructions from the command and control server, as well as incoming WhatsApp messages so it can spread.
Sign up today and you will receive a free copy of our Future Focus 2025 report - the leading guidance on AI, cybersecurity and other IT challenges as per 700+ senior executives
When messages are received through WhatsApp, the malware scans for these and automatically sends a reply on the user’s behalf which includes the malicious link. This is accompanied with a message asking the contact to visit the fabricated Play Store page and download the fake Huawei app.
Stefano also examined the malware to show that it surreptitiously only messages the malicious link to one contact once per hour. This is in order for the app not to arouse suspicions and remain in operation for as long as possible before detection and removal.

Keumars Afifi-Sabet is a writer and editor that specialises in public sector, cyber security, and cloud computing. He first joined ITPro as a staff writer in April 2018 and eventually became its Features Editor. Although a regular contributor to other tech sites in the past, these days you will find Keumars on LiveScience, where he runs its Technology section.
-
 Mobile app security is a huge blind spot for developer teams – 93% are confident their applications are secure, but 62% reported breaches last year
Mobile app security is a huge blind spot for developer teams – 93% are confident their applications are secure, but 62% reported breaches last yearNews Organizations are overconfident about their mobile app security practices, according to new research, and it’s putting enterprises and consumers alike at risk.
-
 APIs: Understanding the business benefits and risks
APIs: Understanding the business benefits and riskswhitepaper What you need to know about potential data exposure from APIs
-
 Apple patches actively exploited iPhone, iPad zero-day and 18 other security flaws
Apple patches actively exploited iPhone, iPad zero-day and 18 other security flawsNews The out-of-bounds write error is the eighth actively exploited zero-day impacting Apple hardware this year and could facilitate kernel-level code execution
-
 Qualcomm and Mediatek flaws left millions of Android users at risk
Qualcomm and Mediatek flaws left millions of Android users at riskNews An open source audio codec used by chipset firms is believed to have put two-thirds of Android users' private calls and files at risk
-
 Businesses on alert as mobile malware surges 500%
Businesses on alert as mobile malware surges 500%News Researchers say hackers are deploying new tactics that put Android and iOS at equal risk
-
 Apple fixes array of iOS, macOS zero-days and code execution security flaws
Apple fixes array of iOS, macOS zero-days and code execution security flawsNews The first wave of security updates for Apple products in 2022 follows a year in which a wide variety of security flaws plagued its portfolio of devices
-
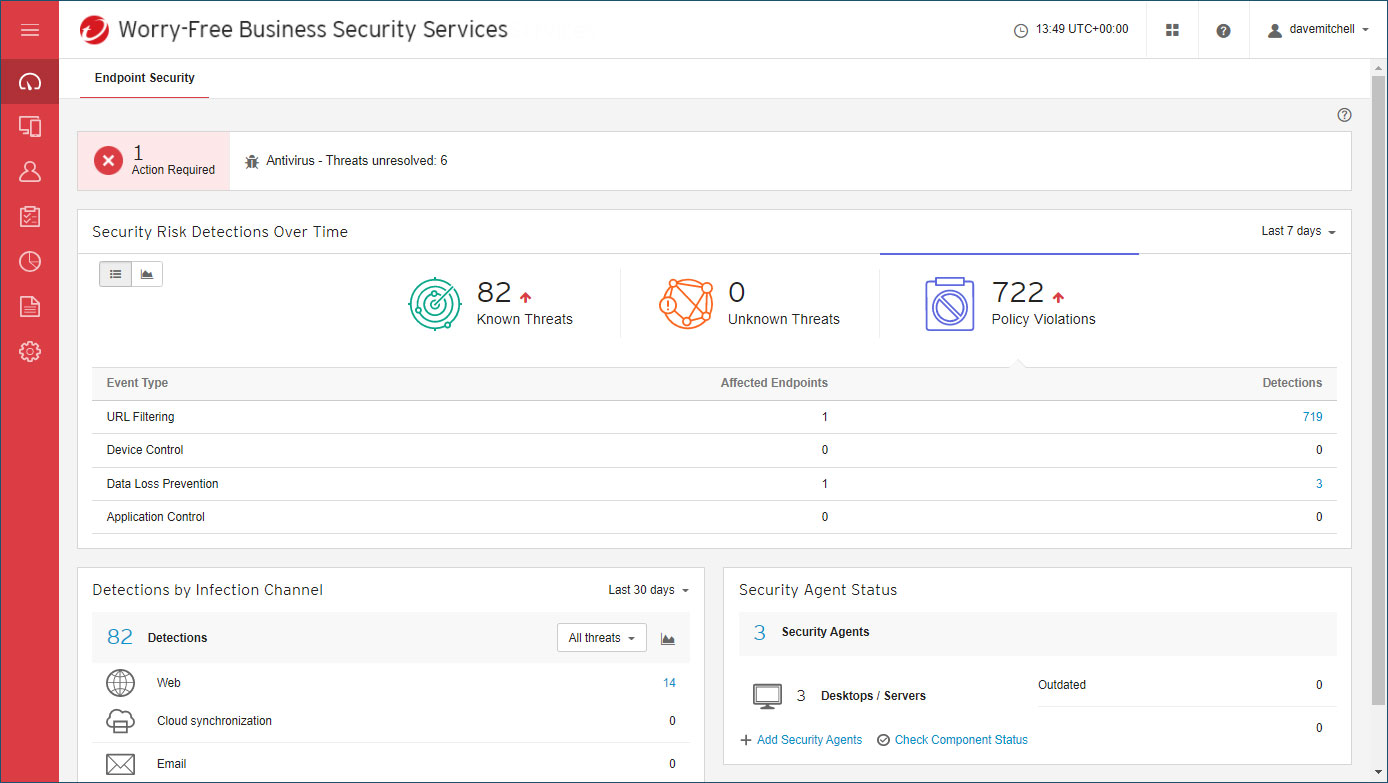 Trend Micro Worry-Free Business Security review: Great cloud-managed malware protection
Trend Micro Worry-Free Business Security review: Great cloud-managed malware protectionReviews A reassuringly simple endpoint-protection solution – although mobile support is basic
-
 Over 300,000 Android users downloaded banking trojan malware
Over 300,000 Android users downloaded banking trojan malwareNews Hackers defeated Google Play restrictions by using smaller droppers in apps and eliminating permissions needed

